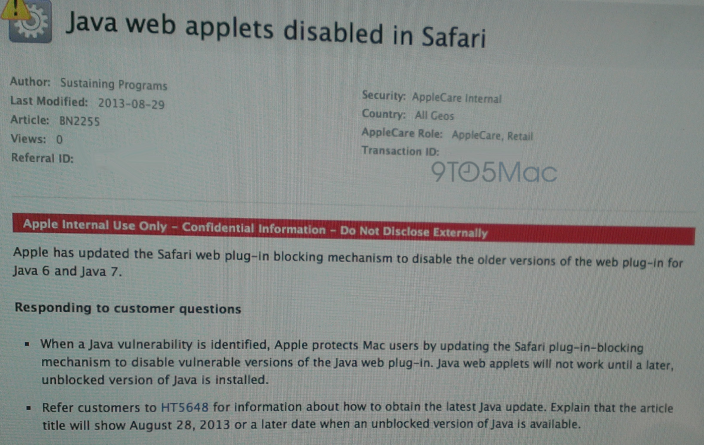
[youtube=http://www.youtube.com/watch?v=YdDrAWxkscM&feature=player_embedded]
Samsung’s Series 7, originally intended for Windows 7, has been hacked to run a Hackintosh version of OS X Lion, a user on the tonymacx86 forums highlighted today. Awkward, considering the whole Samsung vs Apple fight. As you can see in the video above, the version of Lion runs relatively smoothly, but the big issue is an external monitor is needed to display the video. The user highlights the tools needed:
8GB USB KEY, mini-HDMI to HDMI cable/adapter, USB Keyboard and mouse. After you make a UniBeast USB key you have some space still left on it so I made a folder and downloaded MultiBeast 4.1.0: Lion Edition.
If you’ve got a Series 7 laying around and are tired of the bleh Windows, you should definitely try this hack out (if you’ve got the technical know-how). With specs close to the MacBook Air — an 11.6-inch display, 64GB SSD, and i5 processor — this device seems pretty perfect to run full on OS X in a mobile setting. It also gives you a little more horsepower than an iPad 2, though that’s like comparing Apples and Oranges.
For all of the technical details, hit up the tonymacx86 forums. We’ve already shared our thoughts on the Hackintosh community, and we’re certainly proponents of what they’re doing. We’re going to keep an eye out as this project gets more bug fixes, specifically the screen issue. Luckily, the developer says he is committed to working on this project.