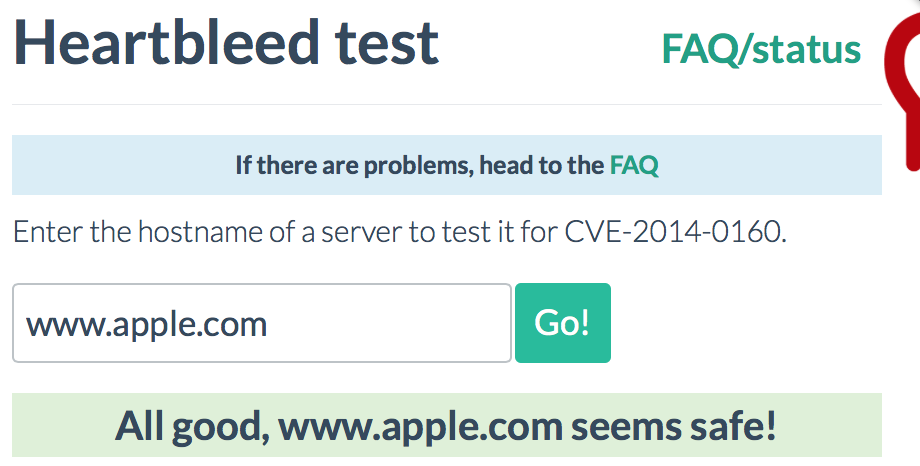
Strange bug has stopped some streaming video apps from playing content
As noted by the BBC, some video apps on iOS have inexplicably stopped working today. Videos simply fail to stream, resulting in error messages like the one shown above. The cause of the issue is still unclear, but the bug is affecting multiple high-profile apps in the UK such as BBC iPlayer and Sky Go. Whether the issue is more widespread is not yet known.
It is unknown whether the bug is an issue with Apple’s software or with the third-party app developers. However, as both independent services have failed on the same day it seems like the problem lies with iOS itself. Setting the date on your iPhone or iPad to the past will make videos play again, which suggests the error may be related to expired digital certificates.