A scandal surrounding the use of NSO’s Pegasus spyware by Israel’s police has provided a rare look at early screenshots of the app in action when remotely accessing a compromised smartphone.
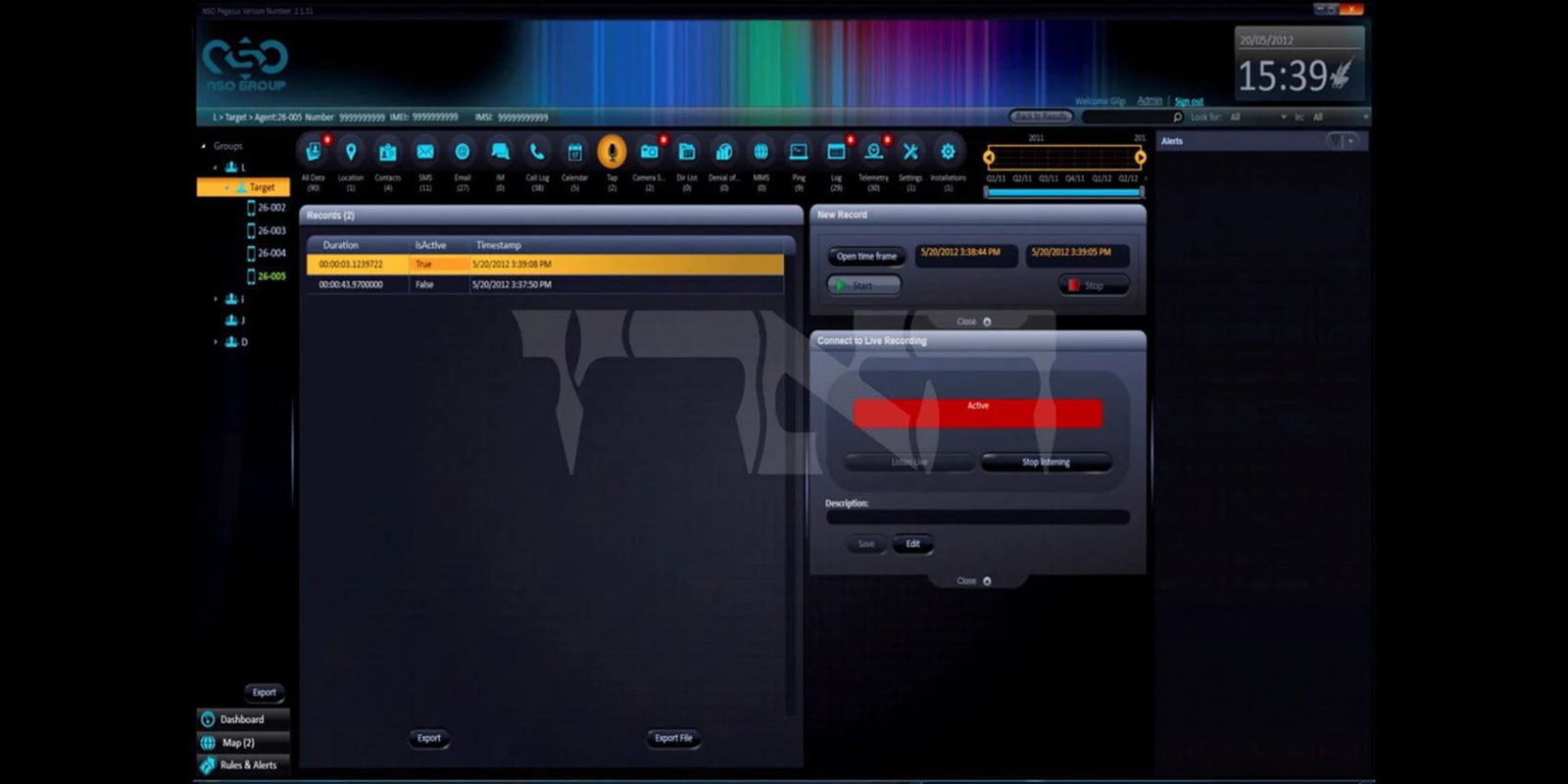
A series of screenshots show the spyware doing everything from displaying the contents of WhatsApp messages to activating the camera to spy on the owner’s surroundings …
Quick Pegasus primer
Here’s our quick Pegasus primer for anyone unfamiliar.
NSO Group makes spyware called Pegasus, which is sold to government and law enforcement agencies. The company purchases so-called zero-day vulnerabilities (ones that are unknown to Apple) from hackers, and its software is said to be capable of mounting zero-click exploits – where no user interaction is required by the target.
In particular, it’s reported that simply receiving a particular iMessage – without opening it or interacting with it in any way – can allow an iPhone to be compromised, with personal data exposed.
NSO sells Pegasus only to governments, but its customers include countries with extremely poor human rights records – with political opponents and others targeted.
The US government banned the import and use of Pegasus, depriving the company of its most lucrative customer base: US law enforcement agencies. Apple added to the pressure, suing the company, and alerting owners of infected iPhones. That put the company under extreme financial pressure, which may see it disappear – or may just make things worse.
Pegasus screenshots
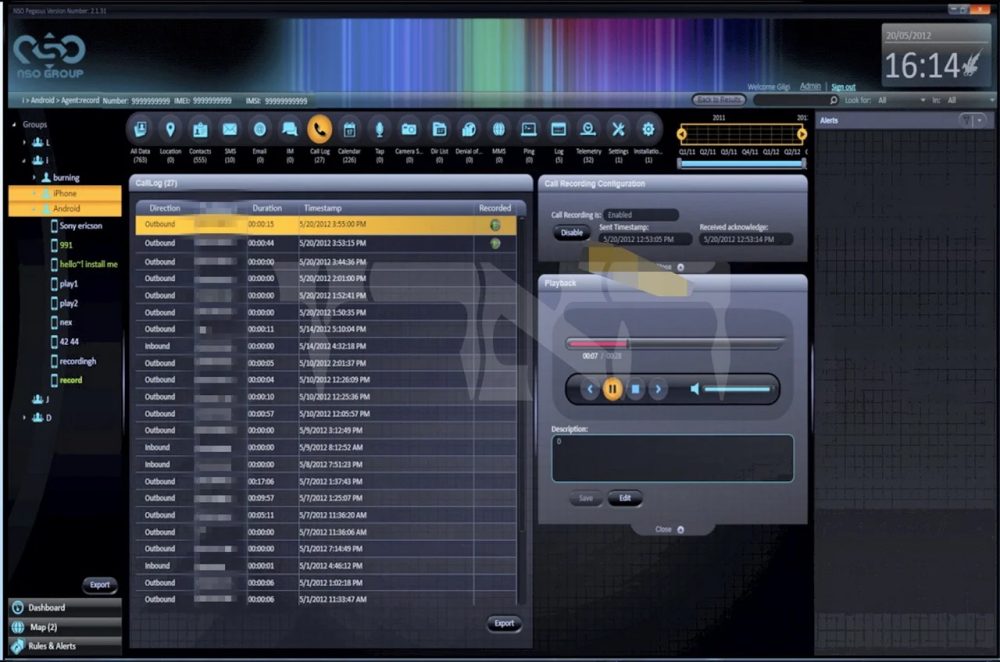
The screenshots (above and below) came to light as a result of investigative journalism by the financial publication Calcalist into potentially illegal use of Pegasus by police within Israel. They show:
- Activating the phone’s microphone to listen in live to the owner and anyone with them
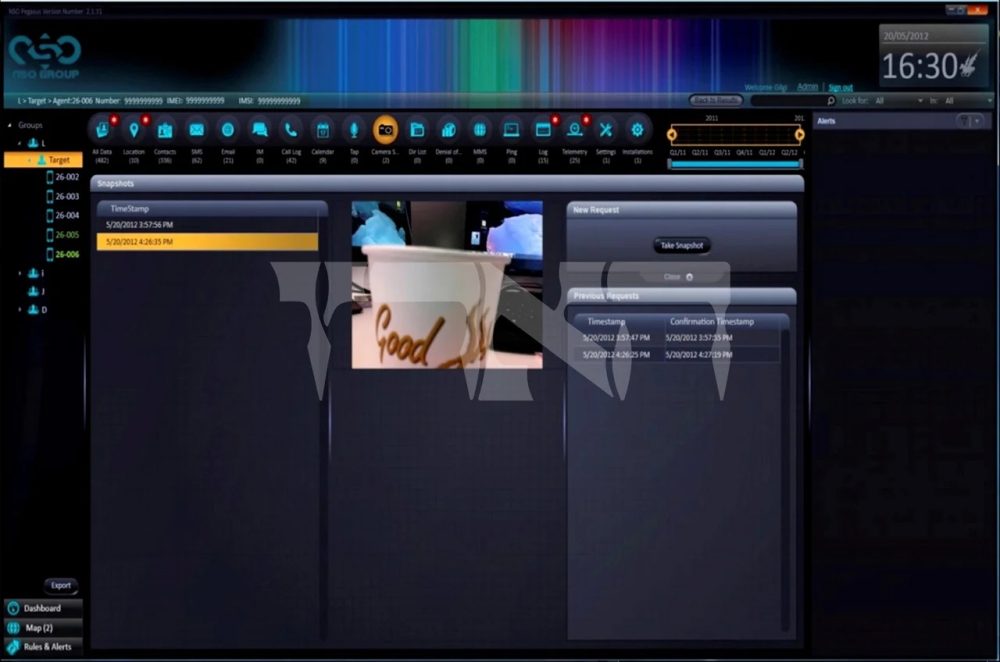
- Activating the phone’s camera to take snapshots of the surroundings
- Listening to captured recordings of incoming & outgoing phone calls
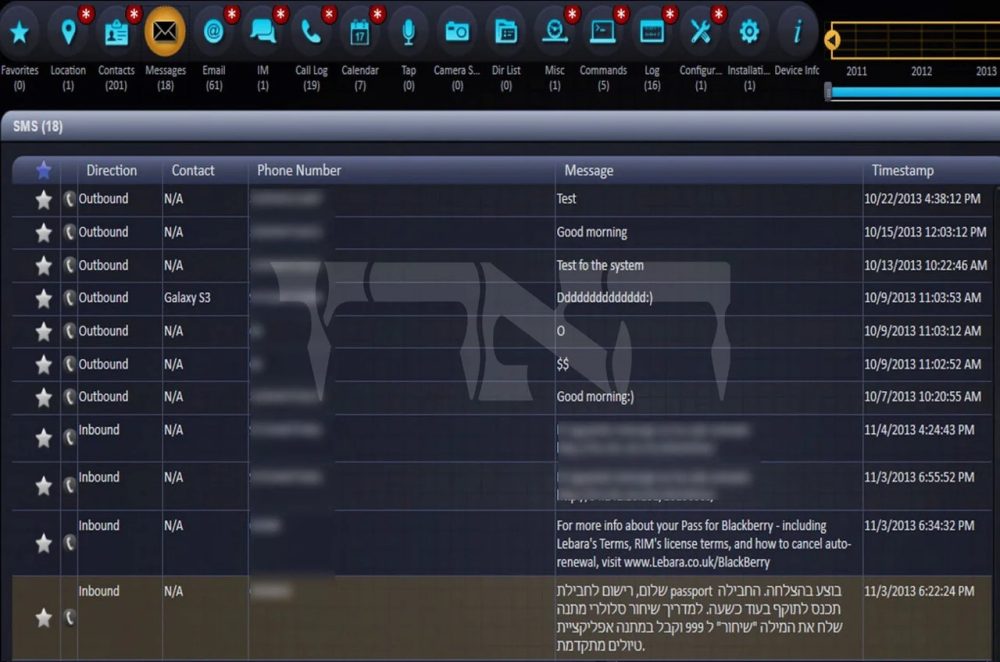
- Reading text messages
- Reading WhatsApp messages
This resulted in an official investigation led by deputy attorney General Amit Merari, with the report including a presentation prepared for the cabinet of the government at the time. The slide deck was designed to show how police were using the spyware, though it is not yet known whether it was ever actually presented to ministers.
Haaretz reports on the capabilities shown in the presentation.
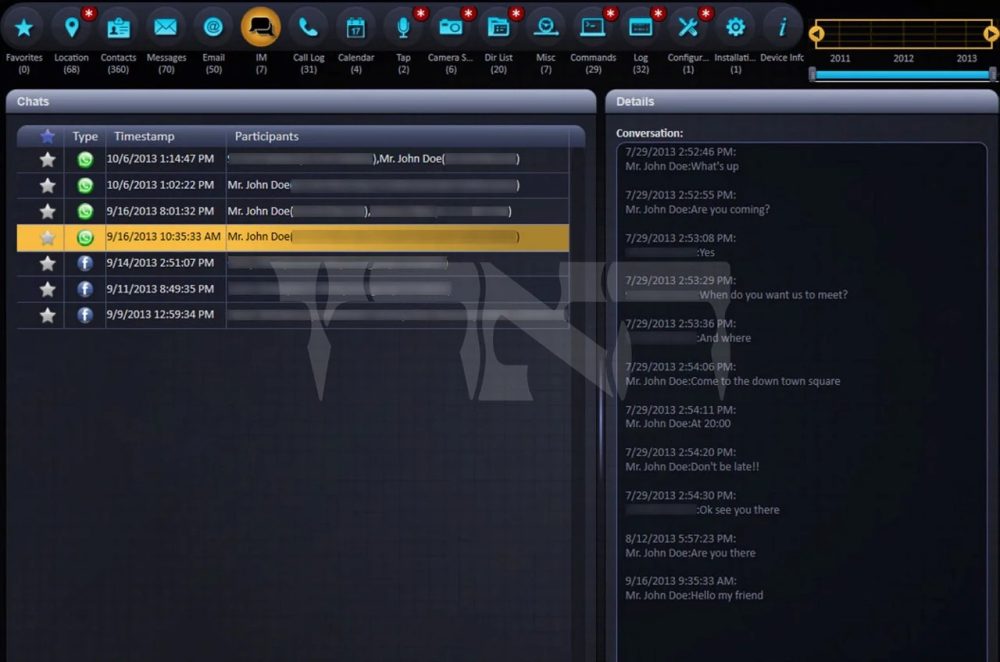
The screenshots demonstrate the wide range of tools that the police intended to use as soon as a device was infected. One of the images depicts a WhatsApp correspondence of a certain “John Doe,” with a woman who is identifiable by her name.
The woman was a sales manager at NSO, thus in addition to showing system capability, also showed the connection to the company. This is not the only instance. There are also details of other talks between said John Doe and five additional NSO employees.
Another capability of Seifan mentioned in the presentation is the interception of incoming and outgoing phone calls. Besides this ability, which seems to be relatively routine in the world of intelligence surveillance, there is another one known in the professional parlance as “volume listening” and is considered much more intrusive.
In simple terms it means real time wiretapping to a device’s surrounding through the remote activation of the device’s microphone. This type of wiretapping requires an order from a district court president or their deputy.
The list of capabilities the police intended to outline goes beyond wiretapping and includes remote operation of the camera on the “infected” device, an action that is very likely illegal as the law does not explicitly permit the planting of concealed cameras, and certainly does not permit the remote control of a camera by hacking a suspect’s mobile device.
NSO has had many different versions of Pegasus, and it’s unclear whether this version was ever used outside Israel, but it does align with widely-reported capabilities of a version used within the US. It was knowledge of these kind of capabilities which led to whistleblower Edward Snowden insisting that anyone meeting with him had to place their phone inside a microwave oven to block radio transmissions.
You can see the other screenshots below. Right-click and Open Image in New Tab to see full-size.
FTC: We use income earning auto affiliate links. More.




Comments