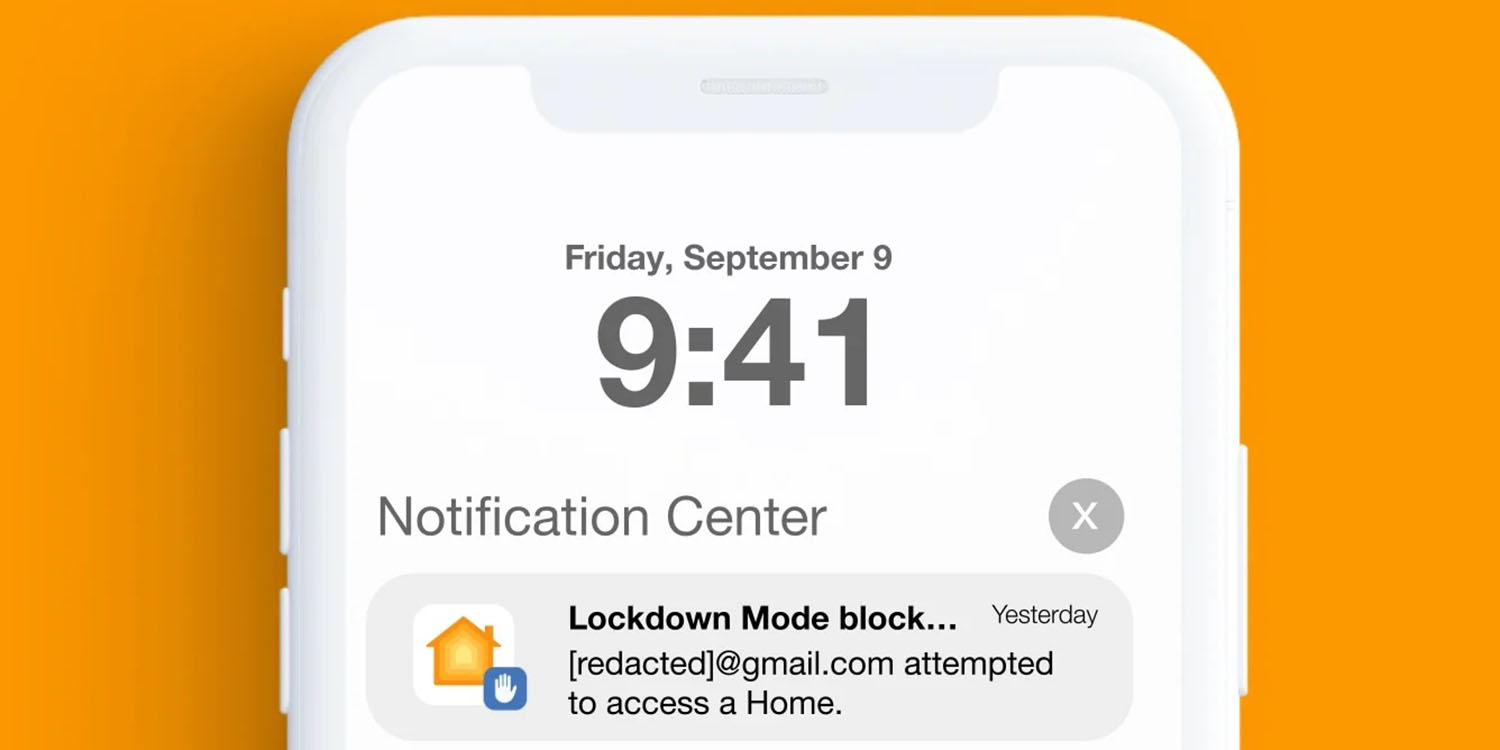
An NSO zero-click iPhone hack worked by gaining access to HomeKit on the device, but it was blocked by those using Apple’s Lockdown Mode security feature, with the phone alerting them to the access attempt.
However, two other NSO zero-click attacks seemingly succeeded – both exploiting vulnerabilities in the Find My app …
Zero-click attacks
Most attacks on devices rely on tricking owners into installing malware by tapping a link. A common tactic is to send a message that appears to be from Apple, PayPal, or similar.
Tech-savvy and security-conscious iPhone users know the signs of this, but there has long been no protection against so-called zero-click attacks. With these, a device can be compromised without the user doing anything at all.
Spyware company NSO has been notorious for using zero-click attacks on iPhones, many of which were used by governments with poor human rights records to spy on political opponents, journalists, lawyers, and human rights activists. In these, simply receiving an iMessage – without even opening it – is enough to give remote access to your iPhone.
Lockdown Mode
To protect those most likely to be targeted by state-sponsored attacks, Apple last year introduced Lockdown Mode – a way of limiting the functionality of an iPhone in ways designed to minimize the risk of a zero-click attack working.
Lockdown Mode is only intended to be used by those who consider themselves to be at serious risk of government surveillance. It greatly reduces the feature set of an iPhone, including blocking most message attachments, disabling many websites, and so on.
Three new NSO zero-click iPhone hacks detected
Security researchers at Citizen Lab have released details of three new NSO zero-click iPhone hacks. They were detected late last year, but the company withheld details until Apple was able to patch iOS to block the attacks.
The attack vector used by two of the three attacks appears to be to send an iMessage containing malware, which then exploits vulnerabilities in other stock Apple apps.
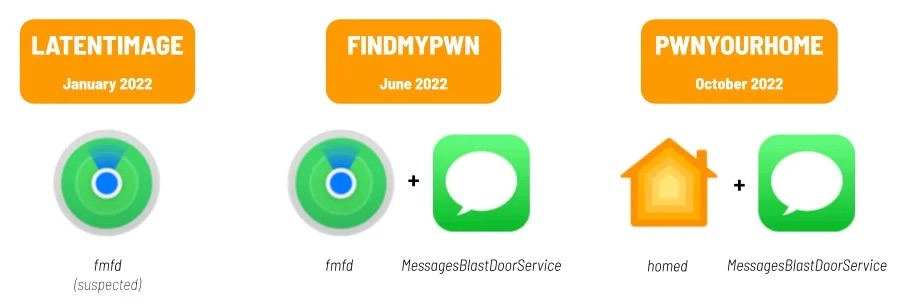
“PWNYOURHOME,” was deployed against iOS 15 and iOS 16 starting in October 2022. It appears to be a novel two-step zero-click exploit, with each step targeting a different process on the iPhone. The first step targets HomeKit, and the second step targets iMessage.
“FINDMYPWN” was deployed against iOS 15 beginning in June 2022. It also appears to be a two-step exploit; the first step targets the iPhone’s Find My feature, and the second step targets iMessage.
We shared forensic artifacts with Apple in October 2022, and additional forensic artifacts regarding PWNYOURHOME in January 2023, leading Apple to release several security improvements to HomeKit in iOS 16.3.1
Once we had identified FINDMYPWN and PWNYOURHOME, we discovered traces of NSO Group’s first 2022 zero-click (“LATENTIMAGE”) on a single target’s phone. This exploit may also have involved the iPhone’s Find My feature, but is a different exploit chain than FINDMYPWN.
The report says that targets who had Lockdown Mode activated were alerted to one of these attacks.
For a brief period, targets that had enabled iOS 16’s Lockdown Mode feature received real-time warnings when PWNYOURHOME exploitation was attempted against their devices. Although NSO Group may have later devised a workaround for this real-time warning, we have not seen PWNYOURHOME successfully used against any devices on which Lockdown Mode is enabled.
It said that the attacks had been used against human rights groups in Mexico. The United Nations reported last year that more than 100,000 people in Mexico have been registered as “disappeared,” and presumed to have been killed by a government with a long history of political opponents vanishing without trace.
FTC: We use income earning auto affiliate links. More.





Comments