9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
Last week, Apple confirmed that users on macOS Sequoia will no longer be able to Control-click to override Gatekeeper to open software that isn’t signed or notarized by the company. This was a slight change with what I believe will have a significant impact. It also gives us a glimpse into what might happen behind the scenes at Apple as Mac malware gets more clever and the amount of it reach all-time highs.

I’ve always been baffled by how easily any non-sophisticated Jonny Appleseed user could bypass Mac’s two best security features (Gatekeeper and XProtect) in just two clicks.
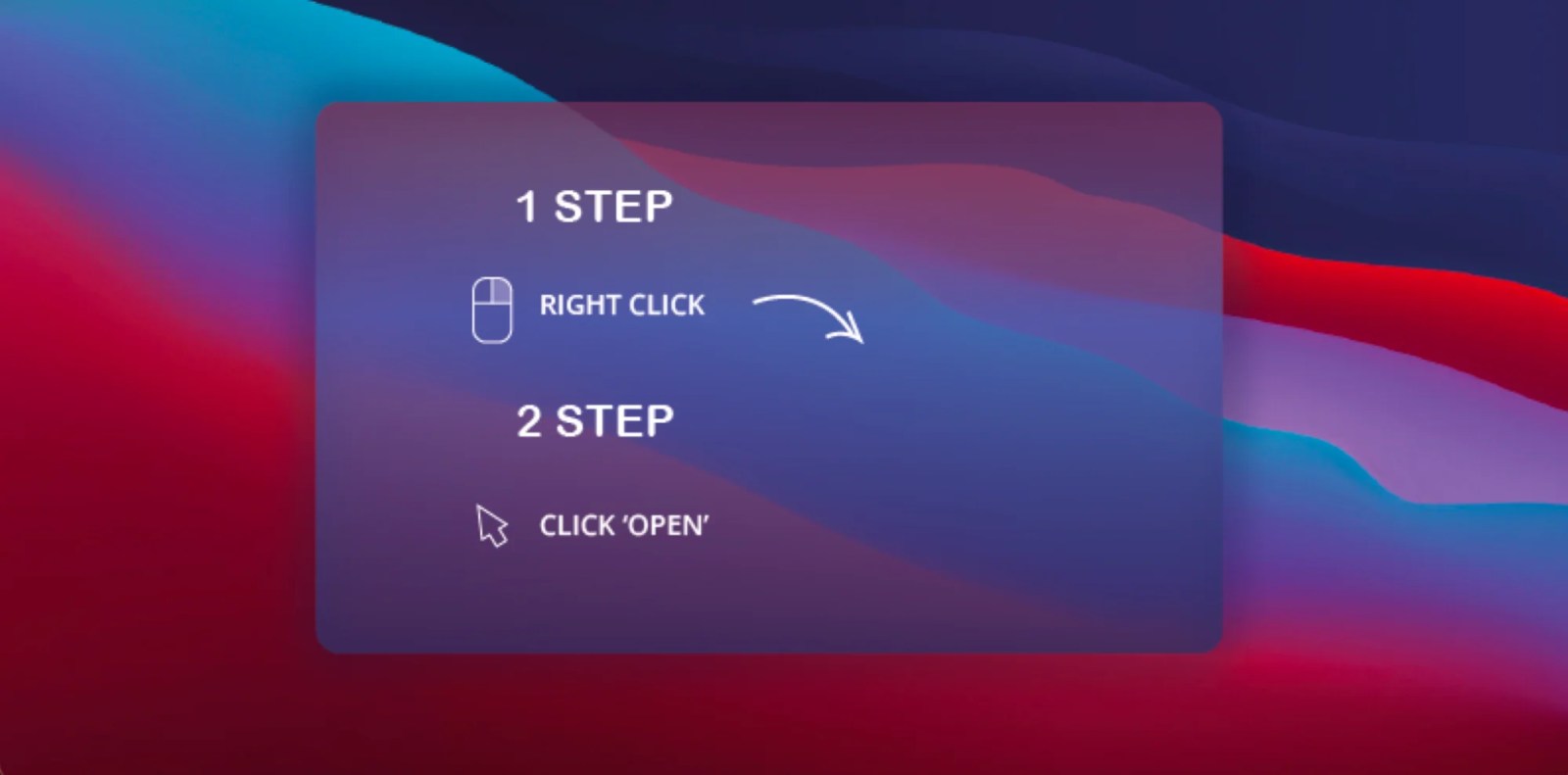
This typically happens when a user attempts to download unsigned software, like a pirated application. When they double-click to open it, macOS will present an error message stating, “[application.pkg] can not be open because it is from an unidentified developer.” From here, the user might let out a quick sigh and Google the problem only to find they just have to right-click the package and hit “Open.”
I understand it’s a bit of a catch-22 to say that “non-sophisticated” users would know how to bypass macOS Gatekeeper and the XProtect suite, let alone find and download pirated software. However, what if they thought they were installing a legitimate app, and that’s how it instructed them to open it?
Malware authors are more clever than ever. One of the latest trends is cloning real applications, often productivity apps like Notion or Slack, and injecting malware somewhere in the code. Authors then create install screens like the one below, instructing the user to right-click and open the malware to get around Gatekeeper. The crazy part is that sometimes users will go on to use these applications for quite some time and never know their system has been infected. Persistence is key for cybercriminals.

Image of Shlayer malware from Jamf.
Now in macOS Sequoia, users will need to independently review the app’s security details in System Settings > Privacy & Security before it is allowed to run. It’s great to finally see Apple taking proactive steps to encourage users to review what they’re installing.
However, is this an indication of how bad malware is getting on the platform? Maybe, but it could also be a move to encourage more developers to submit apps for notarization.
The facts are: In 2023, we witnessed a 50% YoY increase in new macOS malware families. Additionally, Patrick Wardle, founder of Objective-See, told Moonlock Lab that the number of new macOS malware specimens increased by about 100% in 2023 with no signs of a slowdown. And just a few months back, Apple pushed its largest-ever XProtect update with 74 new Yara detection rules.
Regardless, I’ve once brought this up to an employee internally and was not met with much interest. So, I’m glad someone changed their mind, no matter the reason.
More: Apple addresses privacy concerns around Notification Center database in macOS Sequoia
FTC: We use income earning auto affiliate links. More.






Comments