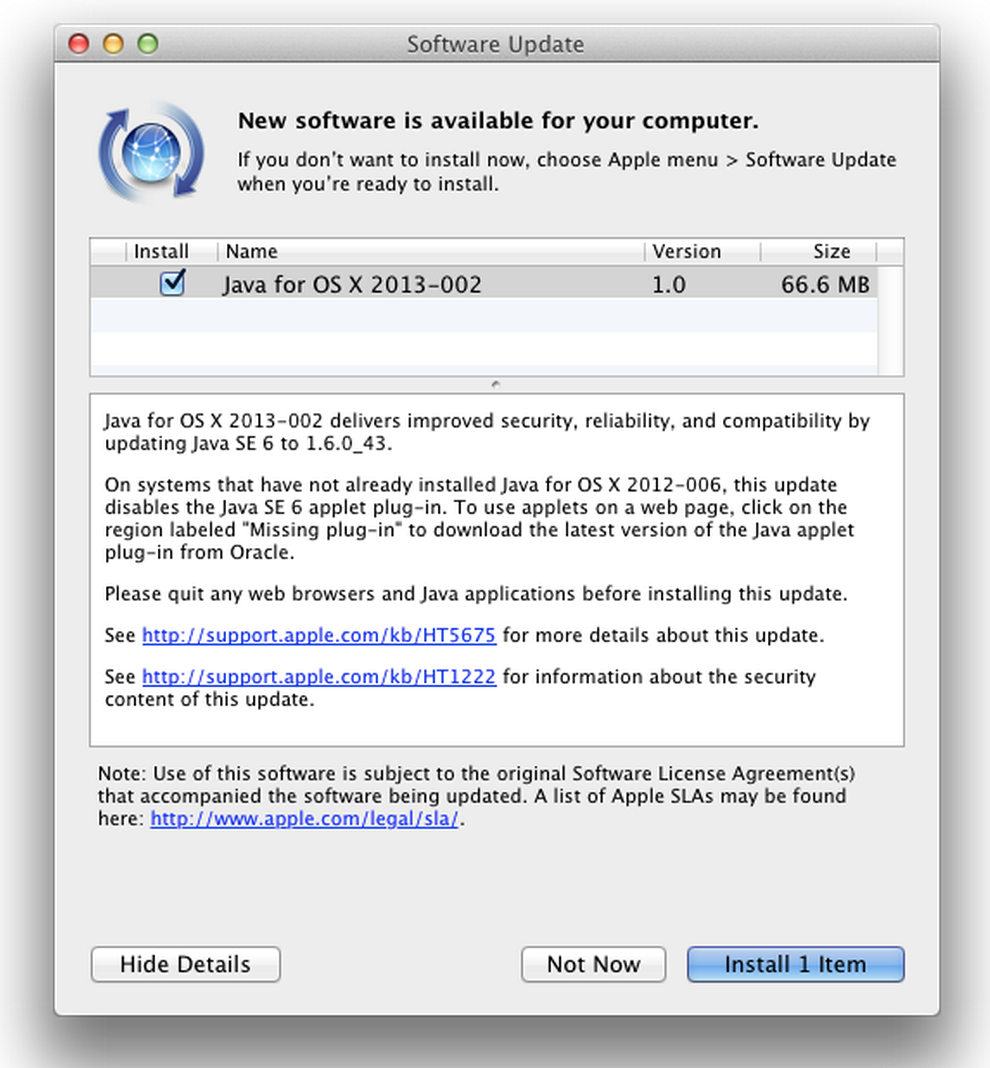
Following a number of reports of new zero-day vulnerabilities in the Java browser plug-in, Oracle has today released an emergency update to Java 7 as Apple updates Java SE 6 to version 1.6.0_43.
Today Oracle released Security Alert CVE-2013-1493 to address two vulnerabilities affecting Java running in web browsers (CVE-2013-1493 and CVE-2013-0809). One of these vulnerabilities (CVE-2013-1493) has recently been reported as being actively exploited by attackers to maliciously install the McRat executable onto unsuspecting users’ machines. Both vulnerabilities affect the 2D component of Java SE. These vulnerabilities are not applicable to Java running on servers, standalone Java desktop applications or embedded Java applications. They also do not affect Oracle server-based software. These vulnerabilities have each received a CVSS Base Score of 10.0.
Researchers from security firm FireEye warned users last week of yet another new Java zero-day vulnerability and recommended users disable Java until Oracle addresses the issue. Today, Oracle said it knew about the flaw since Feb. 1 but didn’t get around to patching it in the last release:
Though reports of active exploitation of vulnerability CVE-2013-1493 were recently received, this bug was originally reported to Oracle on February 1st 2013, unfortunately too late to be included in the February 19th release of the Critical Patch Update for Java SE.
The company intended to include a fix for CVE-2013-1493 in the April 16, 2013 Critical Patch Update for Java SE (note that Oracle recently announced its intent to have an additional Java SE security release on this date in addition to those previously scheduled in June and October of 2013). However, in light of the reports of active exploitation of CVE-2013-1493, and in order to help maintain the security posture of all Java SE users, Oracle decided to release a fix for this vulnerability and another closely related bug as soon as possible through this Security Alert.