We may still be waiting for some developers to update their apps to run natively on M1 Macs, but the developer of SysJoker Mac malware is already on the case.
Security researcher Patrick Wardle points to what he says is the first Mac malware of 2022, and it runs on both Intel and M1 Macs. SysJoker can be controlled remotely by an attacker, allowing it to be used in many different ways …
The malware was discovered by Intezer. Initially it appeared to be Linux-only, but Windows and macOS versions were subsequently identified. Intezer’s own analysis focuses on the Windows version, so Wardle took a deep dive into the macOS variant.
The malware itself is disguised as a video file, but in reality is a universal binary containing both Intel and arm64 builds. The latter means it can run natively on any Apple Silicon Mac.
The malware is essentially a generic app that contacts a server for the payload, meaning it can be used for a wide variety of attacks. It also copies itself to the Library/MacOsServices/ directory so that it will be run each time the Mac is restarted.
The malware appears to have been in use since the middle of last year. Wardle says the good news is that an increasing number of security tools can now detect it, including his own free open-source apps.
Whenever a new piece of malware is uncovered I like to see how Objective-See’s free open-source tools stack up.
Good news (and no really no surprise) they are able to detect and thus thwart this new threat, even with no a priori knowledge of it! Let’s look at how.
First, BlockBlock detects the malware’s launch agent persistence (
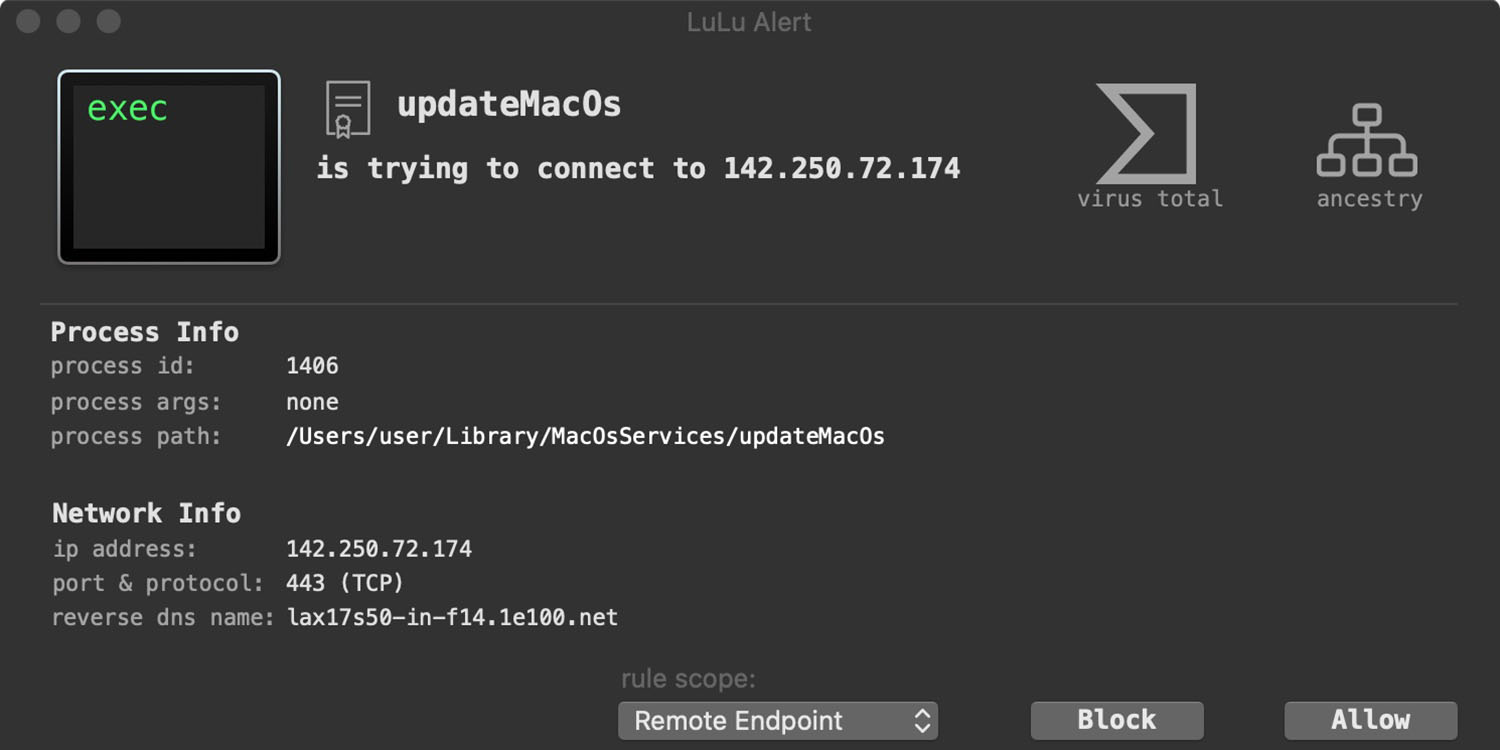
com.apple.update.plist).LuLu, our free, open-source firewall detects when the malware first attempts to beacon out to grab the encrypted address of it’s command and control server.
And if you’re worried that you are already infected? KnockKnock can uncover the malware’s persistence (after the fact).
Mac malware is still relatively rare compared to Windows, but is a growing threat. Much of it is simply adware, doing things like hijacking browsers to display ads hosted by attackers, but SysJoker shows that there are more dangerous examples out there.
As always, the best protection against malware is to follow common-sense precautions. Never open attachments, even from known contacts, unless you are expecting them, and never download anything from a website unless you are confident it can be trusted. However, if you are concerned, then tools like those provided by Wardle offer additional levels of protection.
FTC: We use income earning auto affiliate links. More.




Comments