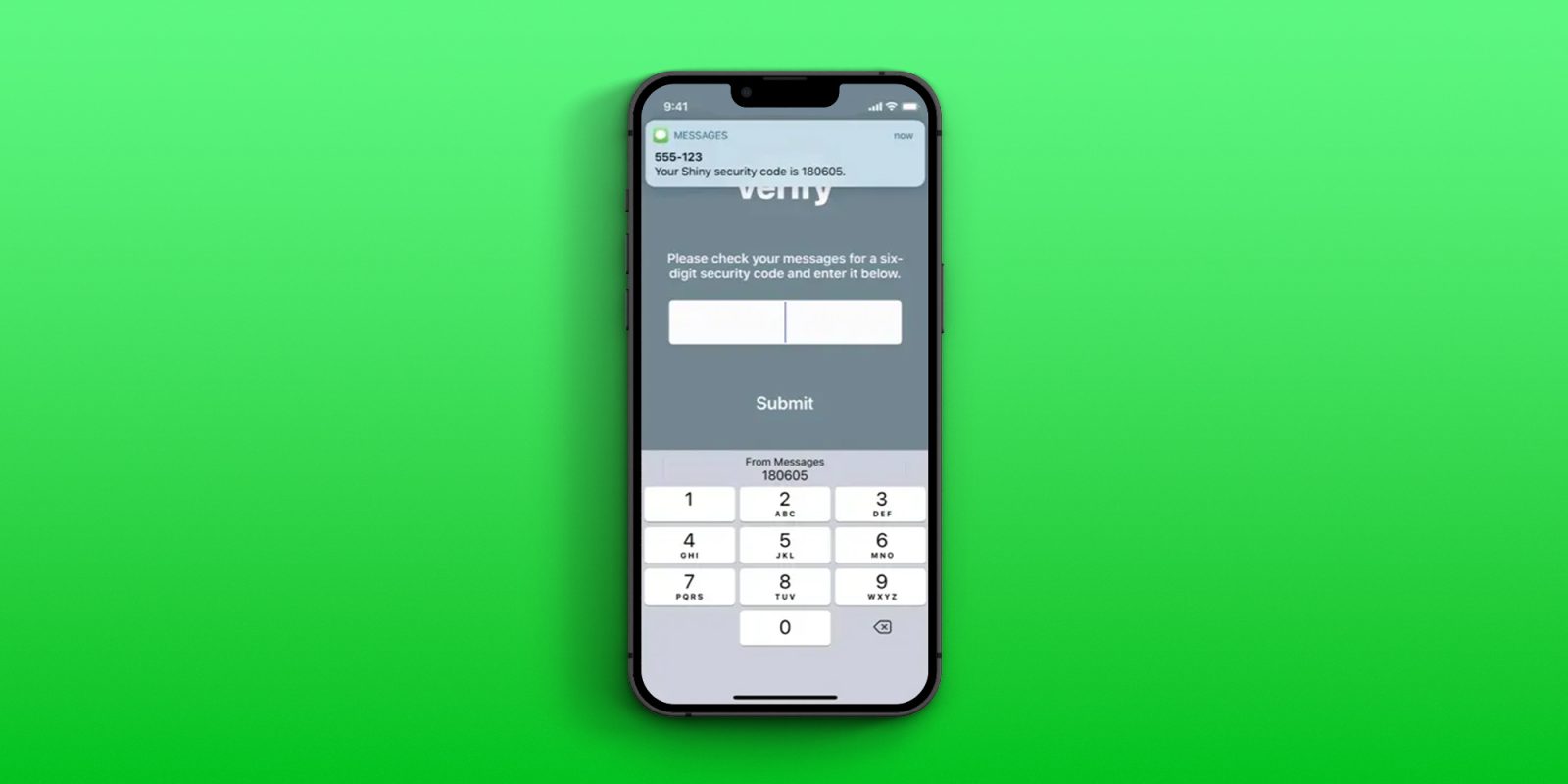
Apple’s two-factor authentication autofill feature makes it painless to enter verification codes sent via SMS, but phishing attackers are getting savvy to this.
When they trick people into clicking on a fake link to a site that prompts for an SMS code, they do the same, so it looks legit when autofill offers to paste it in for you …
But Apple is now guarding against this by asking companies to send SMS codes in a new, more secure format.
With this format, your devices will only offer to autofill a verification code if the domains match. For example, if the site claims to be apple.com but the phishing link is to apple.securelogin.com, then you won’t be offered the autofill option.
The new format, which you may have started to see from late last year, looks like this:
Your Apple ID Code is: 123456. Don’t share it with anyone. @apple.com #123456 %apple.com
Macworld explains the change.
The format generally looks like this:
- A standard human-readable message, including the code, followed by a new line.
- The scoped domain as
@domain.tld. - The code repeated again as
#123456. - If the site uses an embedded HTML element, called an iframe, the source of the iframe is listed after %, such as
%ecommerce.example. (The original spec specifies @; Apple appears to be using % for its texts.)
It’s not a perfect solution. It relies on the user to notice that their device isn’t offering autofill, and for that fact to raise a red flag. It also relies on companies that use SMS-based 2FA to adopt the new format. Finally, as we’ve noted before, SMS is not a secure form of two-factor authentication. Code generators are better, and one is now built into iOS 15.
But every little helps, so if you’re sent an SMS verification code and don’t get offered autofill, take a very close look at the domain name. Better yet, always use your own bookmarks or type URLs rather than clinking on links.
FTC: We use income earning auto affiliate links. More.




Comments