
Twitter’s abrupt rebrand to the letter X is leaving a lot of users confused about the direction of the platform. With this comes an opportunity for cybercriminals, who are now taking advantage of the chaos with some of the most clever phishing emails I’ve ever seen…
Update: Brevo (formally known as Sendinblue) has taken down the mailing list account used by the threat actors. In addition, a security engineer at Twitter confirmed that they are working to address the fake API account.
As a quick refresher, phishing emails are fake emails that can appear to be from a trusted source but are sent by bad actors. They’re designed to trick people into revealing sensitive information or downloading malicious software on a victim’s machine. It is basically the majority of your spam folder.
First pointed out by @fluffypony on Twitter, the new wave of clever phishing emails from x.com target Twitter Blue users, prompting them to migrate their current Blue subscription over to an X one. It’s titled “Preserve your status. Transition smoothly.” While this has all the signs of a legitimate email, it’s not.
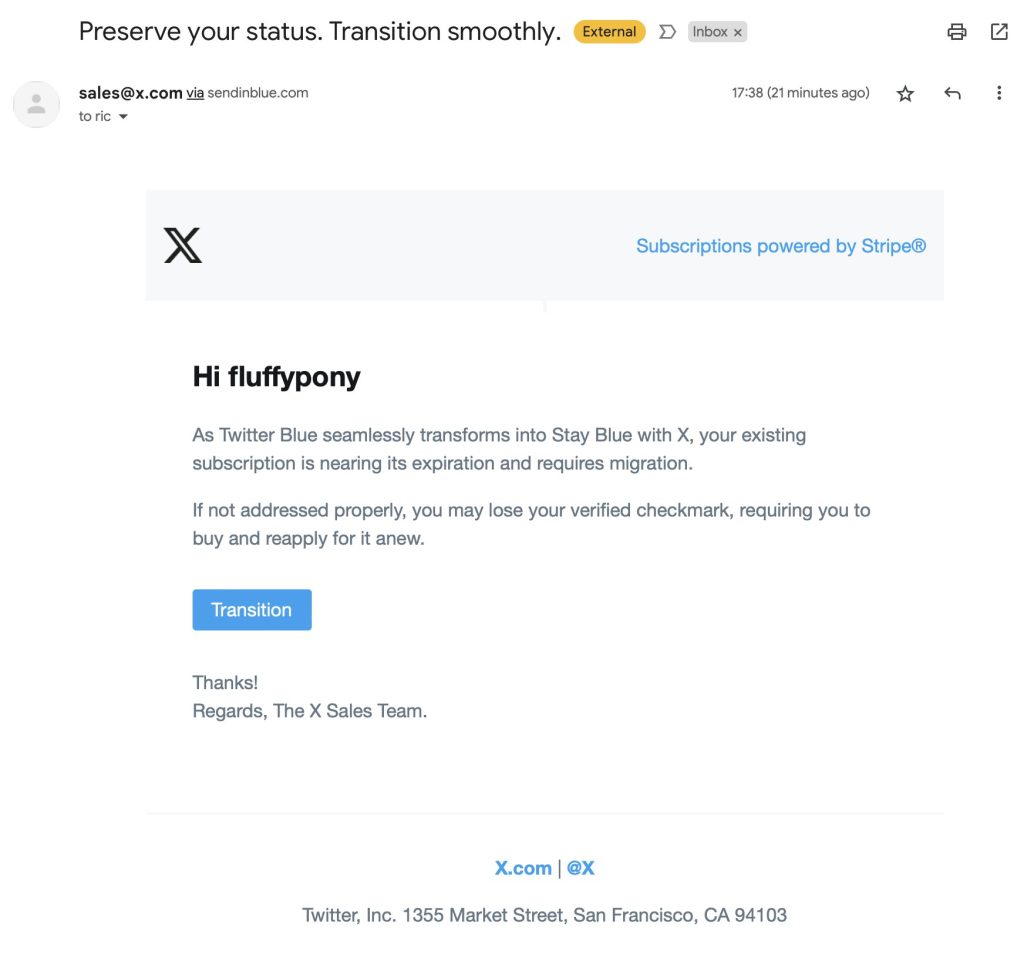
“The most obvious tell of a malicious email is the sender. In this case, it appears to come from sale@x.com, but if you look closer, it was sent from “via sendinblue.com.” This is one of the clever parts.
The cybercriminals used a popular CRM and mailing list platform with a built-in feature to headline a company’s name in bold, followed by “via sendinblue.com.” The goal is for a potential victim to read the bold text and think nothing of it.
The CRM also allows the phishing email to pass through most spam filters.
So, what exactly does the link do?
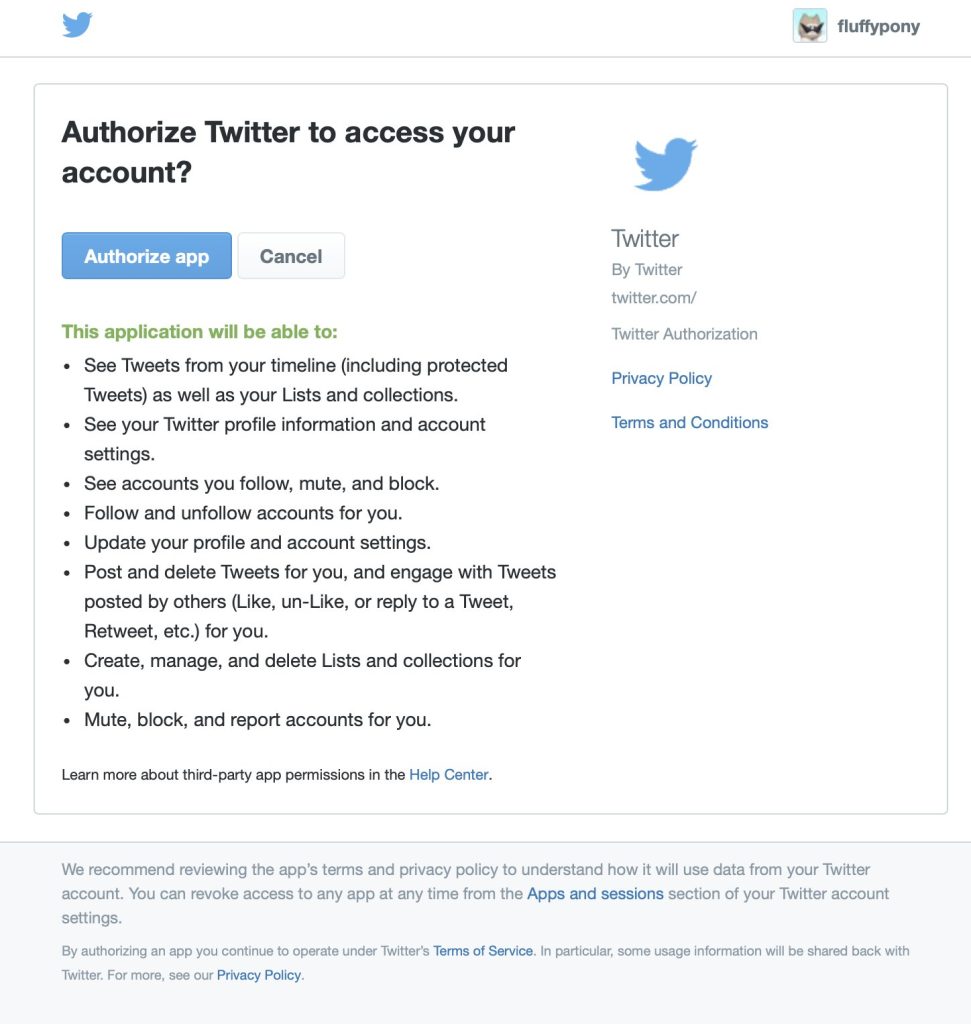
The link directs to a URL housed at a domain that appears to be not affiliated with Twitter or X. Afterwhich, it “redirects you to a (legitimate) API authorization screen, which asks you to authorize an app that appears to be an official Twitter app,” notes @fluffypony.
From here, clicking “Authorize app” would give the threat actors almost full control of your Twitter account. Including the ability to make tweets, update your profile and account settings, and more. This could ultimately end up with your account completely taken over.
It’s clear cybercriminals still see value in verified accounts and the individuals and businesses to whom they may belong to. This could very well be a case of a threat actor booting someone out of their account only to turn around and resell it to another party.
What can I do if I authorized it?
If you have fallen victim to this phishing email or anything similar to it, immediately follow these steps to secure your account:
- Go to Twitter settings -> Security and account access -> Apps and sessions -> Connected apps -> And revoke app permissions to the fake Twitter app or any that you do not recognize.
- Next, change your Twitter password and enable 2-step authentication (non-SMS if possible, OTP is best).
FTC: We use income earning auto affiliate links. More.





Comments