
Security researchers have pulled the curtain back on what appears to be a variant of the infamous RustBucket malware that targets macOS systems. What was first detected earlier in April, a new report from Jamf Threat Labs highlights how this attack continues to evolve and who its potential targets may be.
RustBucket is a relatively new form of malware that specifically targets Mac users. It is the work of an Advanced Persistent Threat (APT) group out of North Korea called BlueNoroff, a sub-group of the nation-state’s well-known cybercrime enterprise Lazarus Group.
On Tuesday, Apple security experts at Jamf Threat Labs revealed details on what it believes to be a new later-stage macOS malware variant being tracked as ObjCShellz from BlueNoroff that closely aligns with RustBucket. “Later-stage” refers to after the initial infection occurs and often involves data exfiltration, establishing persistence, or lateral movement within a network.
BlueNoroff often reaches out to potential victims under the disguise of an investor or company head hunter, according to Jamf. It’s also not uncommon for threat actors to create domains that appear to belong to a legitimate crypto company to blend in with network activity.
The discovery of ObjCShellz (RustBucket-like variant) was made after Jamf researchers found a macOS universal binary communicating with a domain previously classified as malicious.
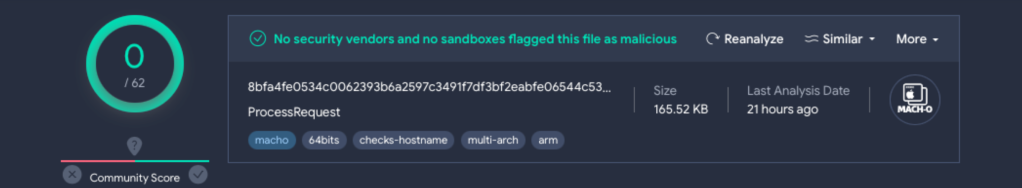
“This executable was undetected on VirusTotal at the time of our analysis, piquing our interest,” Jamf stated.
RustBucket compromises its targets using various techniques, such as phishing emails, malicious websites, and drive-by downloads. Once infected, the malware communicates with command and control (C2) servers to download and execute various payloads. What’s most elusive, however, is its ability to pass through antivirus scanners, like VirusTotal, completely undetected.
And that’s what this new variant did.
In an attempt to communicate with the new variant’s C2 server, Jamf researchers performed a DNS pivot from the initial malicious domain and found several more URLs used for communication. Ultimately, they were unsuccessful, and the C2 server immediately went offline shortly after.
“Over the past few months, Jamf Threat Labs has uncovered various malware campaigns orchestrated by this elusive Advanced Persistent Threat actor in an effort to steal digital assets from victims,” Jaron Bradley, Director at Jamf Threat Labs, told 9to5Mac.
“Our latest research sheds light on a previously unreported piece of malware being used by BlueNoroff to establish covert communication channels on compromised systems. This stealthy program allows the attackers to send and receive data while the victim continues to use their computer, evading detection.”
ObjCShellz and similar variants can pose a serious for Mac users. However, there are a few ways to protect yourself.
- Most importantly: Exercise caution when opening email attachments, especially if the sender is unknown. Malware can be delivered through infected attachments.
- Ensure you’re running the latest version of macOS with all the security patch goodness that comes with it. This helps with addressing known vulnerabilities that malware can exploit.
- Install reputable antivirus and anti-malware software on your Mac that also can detect and block malicious websites. While ObjCShellz can indeed go slip through undetected, it’s always good practice to have an extra layer of defense on Mac.
You can find Jamf’s full report on the new malware variant and view the indicators of compromise here.
FTC: We use income earning auto affiliate links. More.







Comments