
Email security today has many shortcomings. It is widely known that email service providers cannot prevent every suspicious email from being received. However, a new study by web browser security startup SquareX reveals how little companies are doing to block malicious attachments and protect users.
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.

By collecting 100 malicious document samples of different types classified into four main groups, researchers discovered that popular email service providers lack one basic security measure: scanning attachments.
It sounds like the early 2000s, but email attachments are still one of the primary ways through which malware, such as viruses, trojans, ransomware, etc., can infect a victim’s machine. These attacks continue to be lucrative vectors for cybercriminals for many reasons, mainly because of the growing popularity of ransomware.
The four malicious document categories were classified as the following:
- Original Malicious Documents from Malware Bazaar
- Slightly Altered Malicious Documents from Malware Bazaar, such as changes in
metadata and file formats - Malicious Documents modified using attack tools that have existed for many years
- Basic Macro-enabled Documents that execute programs on user devices
First reported by Forbes, researchers took samples, attached them to emails, and sent them through Proton Mail to addresses on iCloud Mail, Gmail, Outlook, Yahoo! Mail, and AOL, part of the Yahoo! group. Notably, if the emails were delivered successfully to the users, they might be vulnerable to any potential threat contained within those attachments.
The table below summarizes the results of sending 7 of the 100 malicious samples to the various email providers, indicating whether the malicious attachment was delivered. “If an email was undelivered, it is a sign that malware was detected when the email was being processed by the server,” according to the study from SquareX.
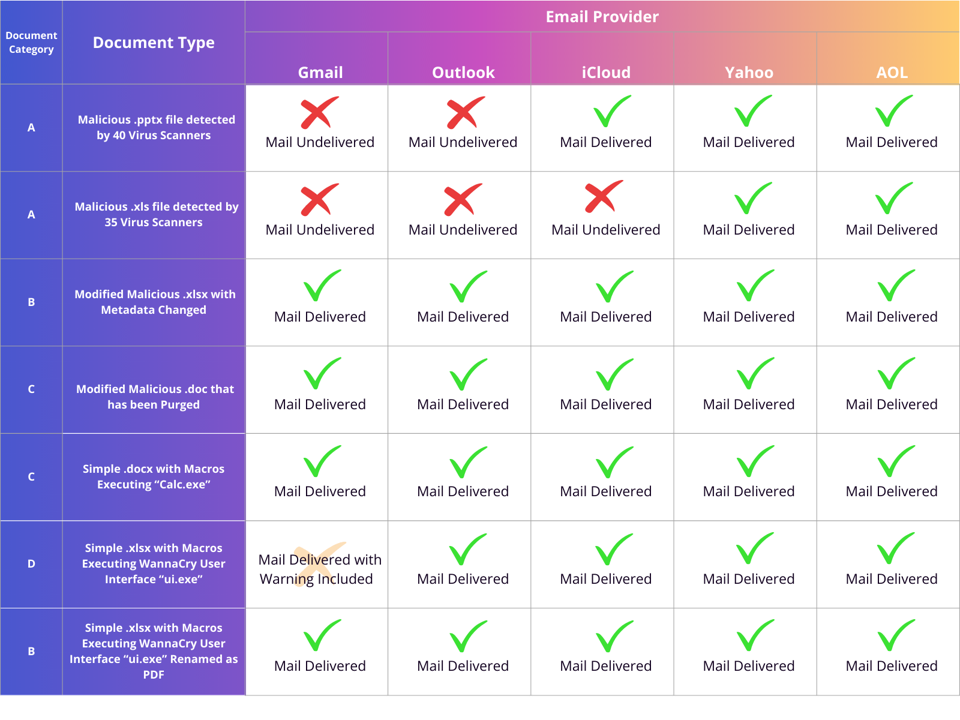
via SquareX
The dilemma
Investing in robust email security features may seem like the obvious critical part for protecting users. However, Ian Thornton-Trump, CISO with threat intelligence solutions firm Cyjax, told Forbes, “this is akin to asking the free Wi-Fi at a Starbucks why are they not blocking more or all cyber attacks.” He further explained that it’s tough to balance free and secure in the same sentence.
Thornton-Trump argues that adding advanced email security features “can be deeply problematic with false positives, which may involve the use of technical support resources to help or fix—that expense across millions of users on a free platform may be commercially untenable.”
Moreover, others argue email providers are dragging their feet on something that could cost substantial resources and impact their bottom line.
What do you think? Let us know in the comments below.
More in security
- Security Bite: This GTA 6-disguised macOS malware performs heist on Keychain passwords
- Apple users targeted by sophisticated phishing attack to reset their ID password
- Here’s how to protect against iPhone password reset attacks
- TikTok national security briefings “deeply troubling” and should be made public – senators
FTC: We use income earning auto affiliate links. More.





Comments