
T-Mobile has suffered another data breach, this time carried out by young hackers that were part of the LAPSUS$ group. While T-Mobile has said that no customer or government information was compromised, it appears LAPSUS$ gained access to T-Mobile’s source code repositories along with its customer account management system.
Reported and seen by Krebs on Security (via TechCrunch), leaked messages between members in the LAPSUS$ cybercrime group show that they successfully hacked into T-Mobile multiple times last month.
The hackers gained access to T-Mobile’s internal systems by taking over multiple employee accounts with purchases through sites like “Russian Market,” social engineering, and other methods of stealing the information.
The messages reveal that each time LAPSUS$ was cut off from a T-Mobile employee’s account — either because the employee tried to log in or change their password — they would just find or buy another set of T-Mobile VPN credentials. T-Mobile currently has approximately 75,000 employees worldwide.
The LAPSUS$ chats and screenshots show they hacked into T-Mobile’s Atlas customer management system on March 19 and searched for “accounts associated with the FBI and Department of Defense.” But as it turned out LAPSUS$ didn’t have the additional credentials to access that information.
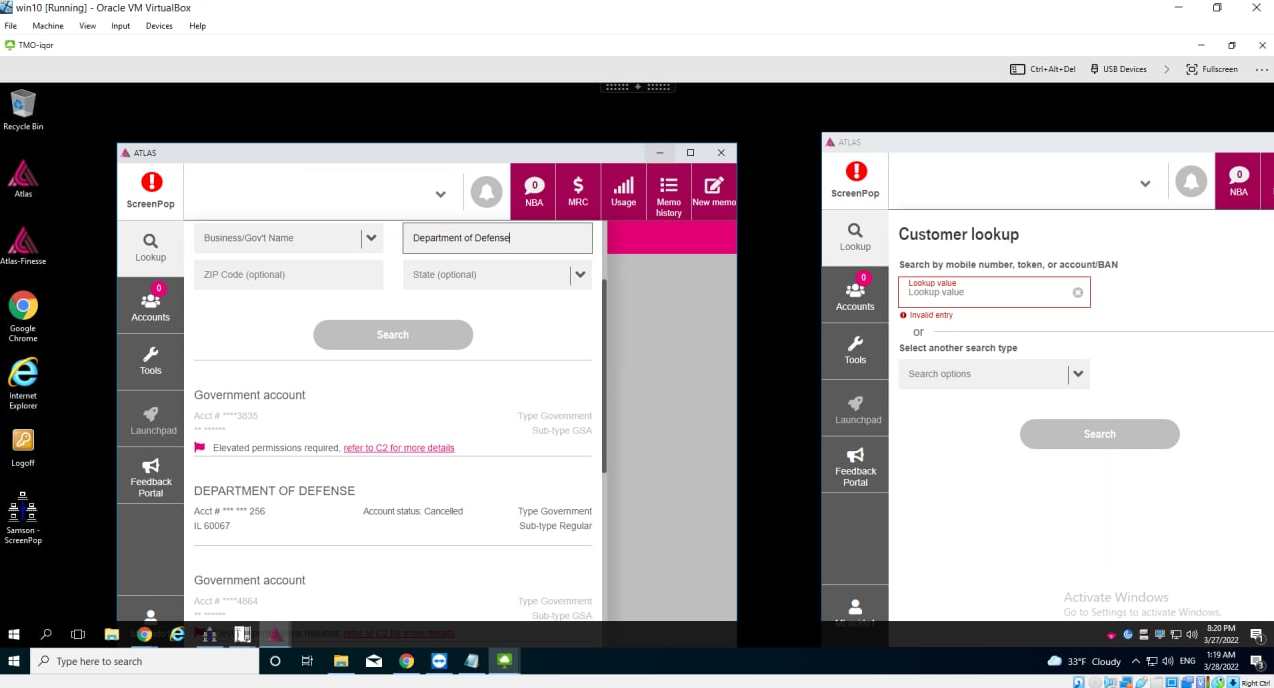
While some of the LAPSUS$ members “desperately wanted to SIM swap some wealthy targets for money,” their 17-year-old leader “White” decided to throw away the VPN access to the Atlas system and pivoted to exploring T-Mobile’s Bitbucket and Slack accounts.
About 12 hours later, “White” shared screenshots showing a script he created had downloaded over 30,000 of T-Mobile’s source code repositories which included content on a variety of the carrier’s projects.
In response to the LAPSUS$ hack, T-Mobile shared the following statement to Krebs on Security:
Several weeks ago, our monitoring tools detected a bad actor using stolen credentials to access internal systems that house operational tools software. The systems accessed contained no customer or government information or other similarly sensitive information, and we have no evidence that the intruder was able to obtain anything of value. Our systems and processes worked as designed, the intrusion was rapidly shut down and closed off, and the compromised credentials used were rendered obsolete.
As for why LAPSUS$ decided to focus on T-Mobile source code instead of making malicious SIM swaps, Krebs on Security thinks they could have been looking for greater security flaws, already had buyers for the source code lined up, or it was potentially just “one big Capture the Flag competition.”
The most active LAPSUS$ members were arrested shortly after the T-Mobile breach.
FTC: We use income earning auto affiliate links. More.






Comments