
Security is a never-ending mission and today Apple has announced its latest innovation for protecting iMessage. Already live in the iOS 17.4 beta is an innovative post-quantum cryptographic protocol called PQ3. The novel upgrade gives iMessage “the strongest security properties of any at-scale messaging protocol in the world.” Here’s why iMessage quantum security is important now and into the future, how PQ3 works, and more.
iMessage has a history of strong security. From the launch in 2011 with end-to-end encryption to the adoption of Elliptic Curve cryptography in 2019 to BlastDoor with iOS 14, and recent improvements like Contact Key Verification at the end of 2023, Apple is constantly upgrading iMessage security.
Now Apple has unveiled what it calls the “most significant” cryptographic security upgrade for iMessage with a complete rebuild of the system’s protocol. Apple detailed the new advancement on its Security Research blog this morning.
Today we are announcing the most significant cryptographic security upgrade in iMessage history with the introduction of PQ3, a groundbreaking post-quantum cryptographic protocol that advances the state of the art of end-to-end secure messaging. With compromise-resilient encryption and extensive defenses against even highly sophisticated quantum attacks, PQ3 is the first messaging protocol to reach what we call Level 3 security — providing protocol protections that surpass those in all other widely deployed messaging apps. To our knowledge, PQ3 has the strongest security properties of any at-scale messaging protocol in the world.
iMessage quantum security
Signal was the first at-scale messaging platform to announce a post-quantum cryptography (PQC) security enhancement last fall with a “key establishment” mechanism.
However, Apple’s approach has two layers of security with PQC key establishment as well as ongoing PQC rekeying.
There isn’t yet an industry standard for rating classical vs PQC cryptography protocols so Apple has developed its own ranking system. Here’s how that looks and how PQ3 got its name as a level 3 PQC:
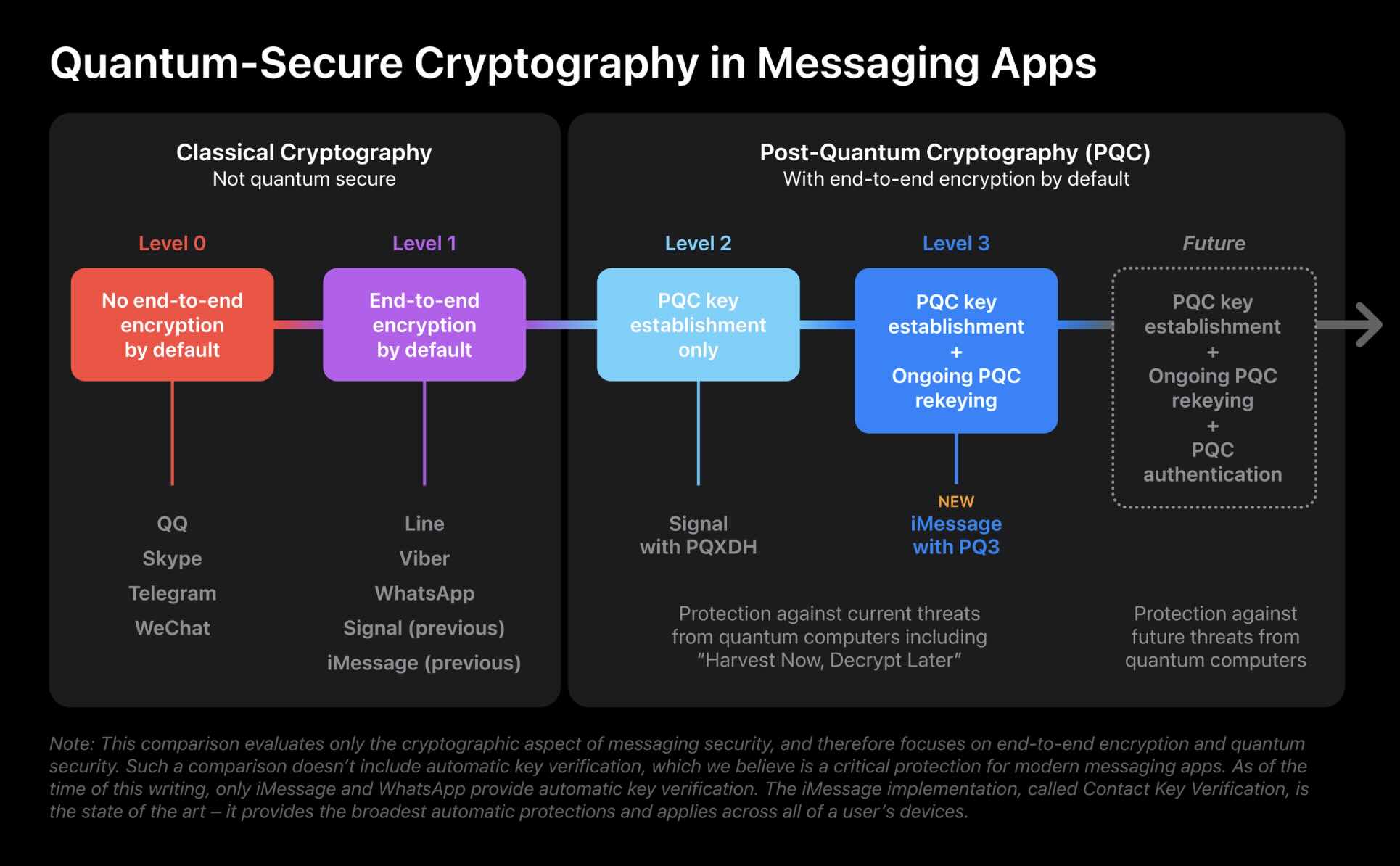
Apple says that Signal’s move to include PQC key establishment (level 2) “is a welcome and critical step” that pushed its security above all other messaging platforms. However, it can only offer quantum security if the conversation key remains uncompromised.
At Level 2, the application of post-quantum cryptography is limited to the initial key establishment, providing quantum security only if the conversation key material is never compromised. But today’s sophisticated adversaries already have incentives to compromise encryption keys, because doing so gives them the ability to decrypt messages protected by those keys for as long as the keys don’t change. To best protect end-to-end encrypted messaging, the post-quantum keys need to change on an ongoing basis to place an upper bound on how much of a conversation can be exposed by any single, point-in-time key compromise — both now and with future quantum computers.
That’s where Apple’s PQ3 (level 3) protocol comes in which secures both the initial key and ongoing rekeying. Importantly, that gives iMessage “the ability to rapidly and automatically restore the cryptographic security of a conversation even if a given key becomes compromised.”
As shown above, Apple envisions future levels of quantum security will include PQC authentication along with PQC key establishment and ongoing rekeying.
Why is post-quantum cryptography important now?
While many security experts believe we’re still around a decade or more to see the full capabilities of quantum computers – like cracking classical cryptography – there are important steps to take now to protect against future attacks on today’s data.
Apple highlights a malicious tactic called “Harvest Now, Decrypt Later” that PQ3 will help protect against.
A sufficiently powerful quantum computer could solve these classical mathematical problems in fundamentally different ways, and therefore — in theory — do so fast enough to threaten the security of end-to-end encrypted communications.
Although such quantum computers don’t yet exist, extremely well-resourced attackers can already prepare for their possible arrival by taking advantage of the steep decrease in modern data storage costs. The premise is simple: such attackers can collect large amounts of today’s encrypted data and file it all away for future reference. Even though they can’t decrypt any of this data today, they can retain it until they acquire a quantum computer that can decrypt it in the future, an attack scenario known as Harvest Now, Decrypt Later.
And of course, as the rise of quantum computers occurs, already having advanced security in place will help prevent present-day quantum attacks of the future as well as efforts to decrypt stolen data of the past.
When is iMessage quantum security launching?
- PQ3 quantum security for iMessage is available for all users with the public releases of iOS 17.4, iPadOS 17.4, macOS 14.4, and watchOS 10.4
Apple says that “iMessage conversations between devices that support PQ3 are automatically ramping up to the post-quantum encryption protocol.”
And the PQ3 protocol “will fully replace the existing protocol within all supported conversations this year.”
More details on iMessage quantum security (PQ3)
In creating PQ3, Apple says it had five requirements:
- Introduce post-quantum cryptography from the start of a conversation, so that all communication is protected from current and future adversaries.
- Mitigate the impact of key compromises by limiting how many past and future messages can be decrypted with a single compromised key.
- Use a hybrid design to combine new post-quantum algorithms with current Elliptic Curve algorithms, ensuring that PQ3 can never be less safe than the existing classical protocol.
- Amortize message size to avoid excessive additional overhead from the added security.
- Use formal verification methods to provide strong security assurances for the new protocol.
Here are more specifics on the PQC public keys Apple is using:
PQ3 introduces a new post-quantum encryption key in the set of public keys each device generates locally and transmits to Apple servers as part of iMessage registration. For this application, we chose to use Kyber post-quantum public keys, an algorithm that received close scrutiny from the global cryptography community, and was selected by NIST as the Module Lattice-based Key Encapsulation Mechanism standard, or ML-KEM. This enables sender devices to obtain a receiver’s public keys and generate post-quantum encryption keys for the very first message, even if the receiver is offline. We refer to this as initial key establishment.
PQ3 has received two formal verifications from Professor David Basin who leads the Information Security Group at ETH Zürich and is one of the inventors of Tamarin – “a leading security protocol verification tool that was also used to evaluate PQ3.”
The University of Waterloo’s Professor Douglas Stebila who has extensive experience researching post-quantum security for internet protocols has also formally verified PQ3.
Head to Apple’s full article on PQ3 quantum security for iMessage for more technical details on the mechanics of PQC key establishment, PQC rekeying, padding and encryption, authentication, and more.
Top image by 9to5Mac
FTC: We use income earning auto affiliate links. More.






Comments