First OS X ransomware detected in the wild, will maliciously encrypt hard drives on infected Macs [Update: How to fix]

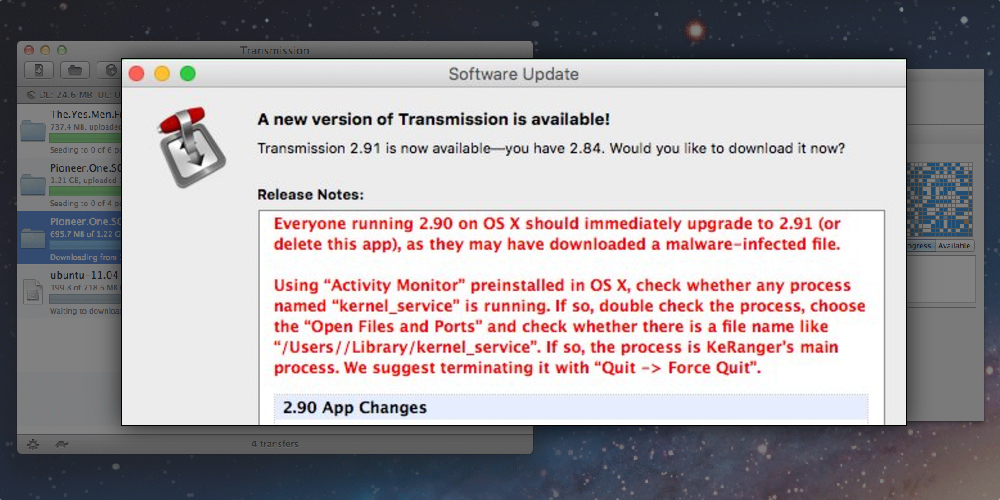
Update: Version 2.92 of Transmission has now been released. This claims to actively remove the ‘KeyRanger’ malware files from the infected Mac.
OS X users have today been hit with the first known case of Mac ‘ransomware’ malware, found in the Transmission BitTorrent client released last week. Infected versions of the app include ‘KeyRanger’ malware that will maliciously encrypt the user’s hard drive after three days of being installed. The malware then asks for payment to allow the user to decrypt the disk and access their data — the ‘ransom’.

![osx-app-screen[1]](http://9to5mac.com/wp-content/uploads/sites/6/2014/05/osx-app-screen1.png)
