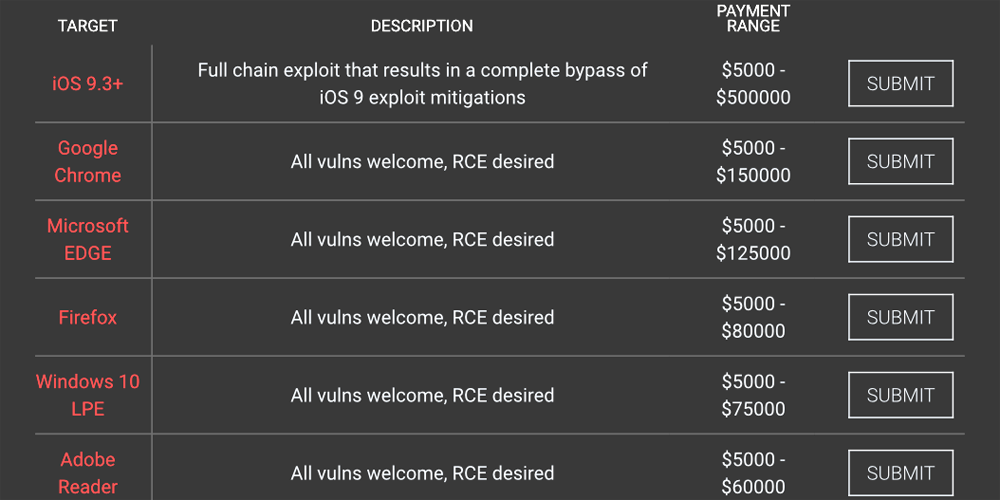
Security company MDSec has been testing a black box device that manages to gain access to iPhones running up to iOS 8.1 by brute-forcing the passcode over a USB connection to simulate keypad entry. Normally, trying every possible 4-digit PIN would be prevented by automated lockout or data wipe after ten incorrect attempts, but the IP Box manages to bypass this.
The IP Box is able to bypass this restriction by connecting directly to the iPhone’s power source and aggressively cutting the power after each failed PIN attempt, but before the attempt has been synchronized to flash memory.
After each attempt, it measures light levels on the screen to see whether it got access to the homescreen; if not, it restarts the phone fast enough that the PIN counter doesn’t get updated.
It’s not a very practical means of attack in the real world. Restarting the phone after every single attempt means that testing every single PIN would take around 111 hours, and thus take an average of around 55 hours to get access. You need physical access to the phone for those 55 hours, and need to have stopped it from gaining any kind of network access in that time to prevent the owner using Find My iPhone to remotely wipe it. But it’s an interesting proof of concept.
Apple appears to have fixed the vulnerability in iOS 8.1.1, as companies selling the kit note that it is not compatible with this version of iOS.
Although this isn’t something to worry about, it’s still good practice to use a complex passcode–not a great hardship on a recent iPhone, where you’ll be using Touch ID most of the time. Just go into Settings > Touch ID & Passcode and slide off the Simple Passcode switch.