Adobe releases emergency Flash security update to address malware attacks on OS X

 .
.
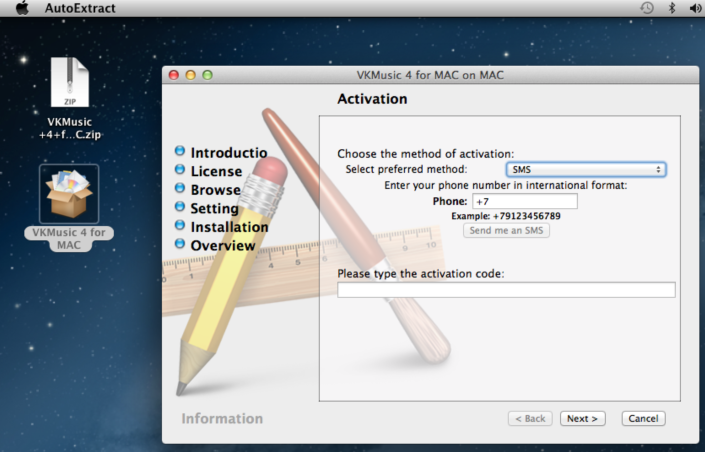
As noted by ArsTechnica, Adobe just released an unscheduled patch to address two vulnerabilities that could be the source of malware attacks on both OS X and Windows. Apple has also issued a KB urging users to update. According to the advisory posted by Adobe, the attacks targeted Firefox or Safari users on Mac:
Adobe is also aware of reports that CVE-2013-0634 is being exploited in the wild in attacks delivered via malicious Flash (SWF) content hosted on websites that target Flash Player in Firefox or Safari on the Macintosh platform, as well as attacks designed to trick Windows users into opening a Microsoft Word document delivered as an email attachment which contains malicious Flash (SWF) content.
The update is available through Adobe’s website here.