Celebgate iCloud phisher pleads guilty to accessing 30+ celebrity accounts, faces 5 years

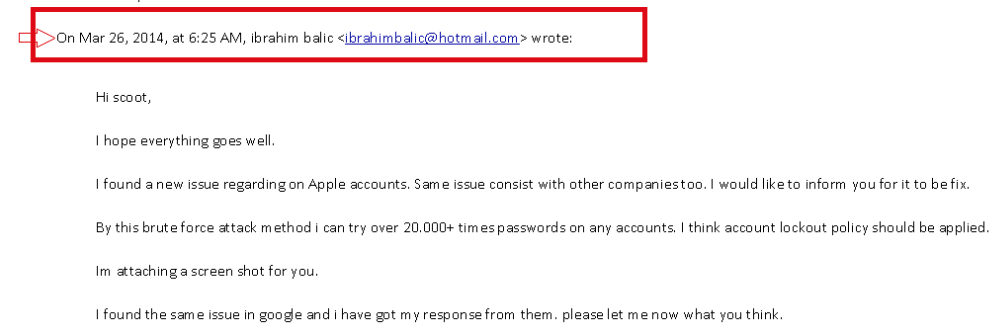
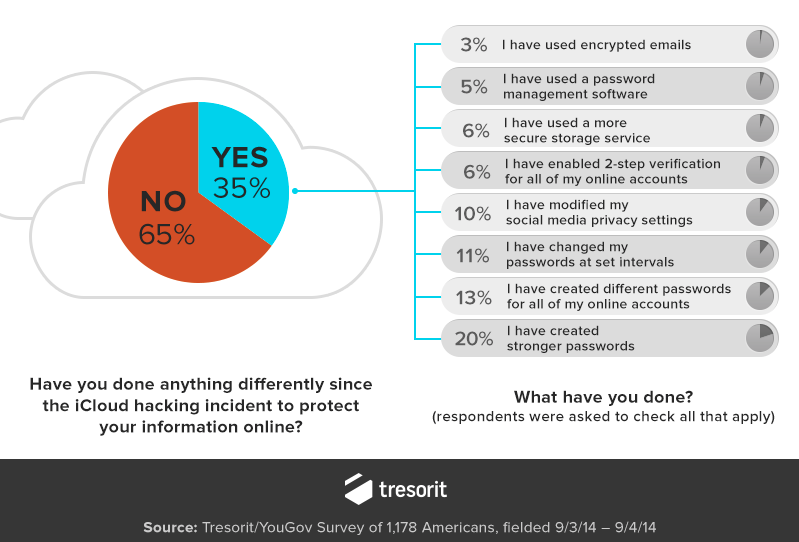
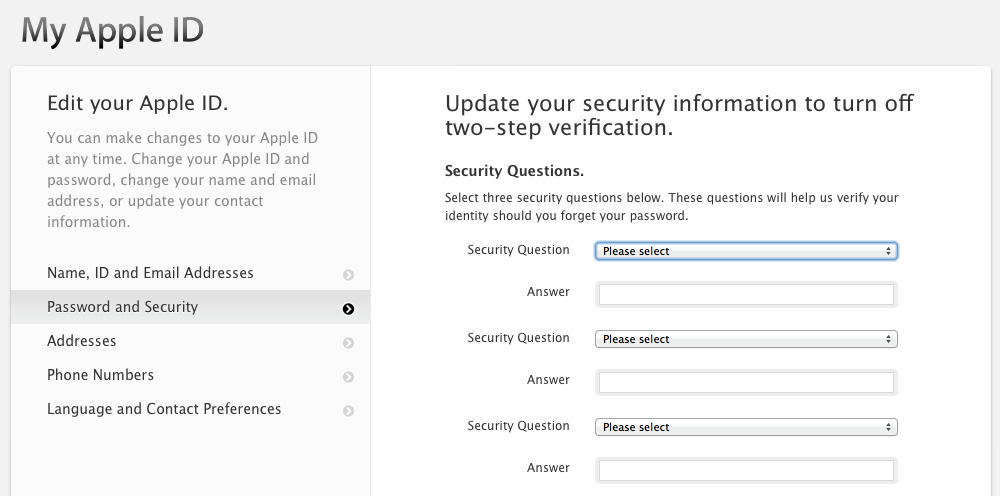
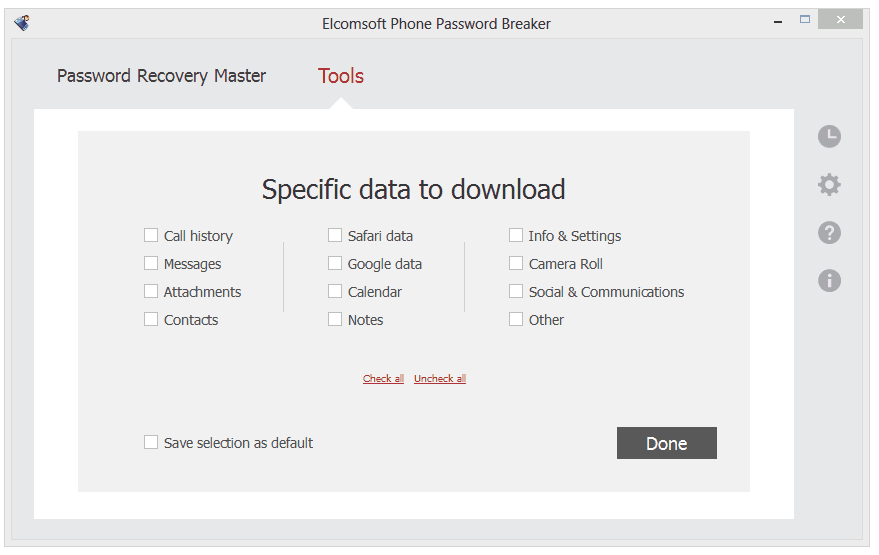
One of the men behind the ‘Celebgate‘ phishing attack has pleaded guilty to accessing more than 300 iCloud and Gmail accounts, including ‘at least 30’ belonging to celebrities. The plea was announced by the U.S. Attorneys Office for the Central District of California.
Edward Majerczyk, 28, who resides in Chicago and Orland Park, Illinois, was named in a criminal information filed today in United States District Court in Los Angeles. Majerczyk has signed a plea agreement in which he agrees to plead guilty to a felony violation of the Computer Fraud and Abuse Act, specifically, one count of unauthorized access to a protected computer to obtain information.
Another of the Celebgate offenders, Ryan Collins, also took a plea back in March in return for a recommended sentence of 18 months …