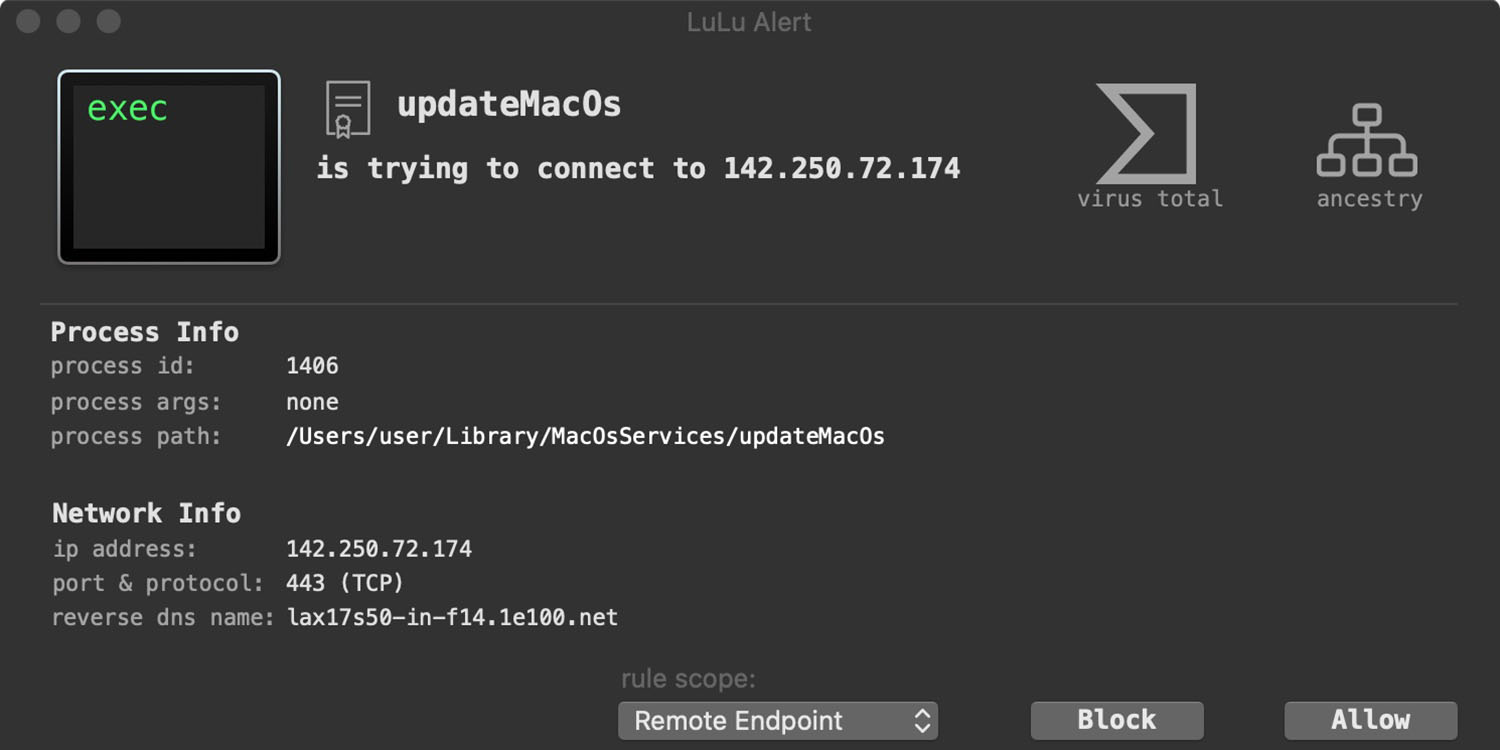
Security Bite: Annual cost of cybercrime to hit $9.2 trillion in 2024

Cybercrime is on an unprecedented rise. A new Statista Market Insights survey predicts that the annual cost of cyberattacks will reach $9.2 trillion this year. For perspective, that’s about one-third of the United States’ GDP or 24 times Apple’s annual revenue in 2023.
Here’s what I’ve learned after calling up a few industry professionals.
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
Expand Expanding Close