Oracle begins bundling Ask adware with Java for Mac installations by default
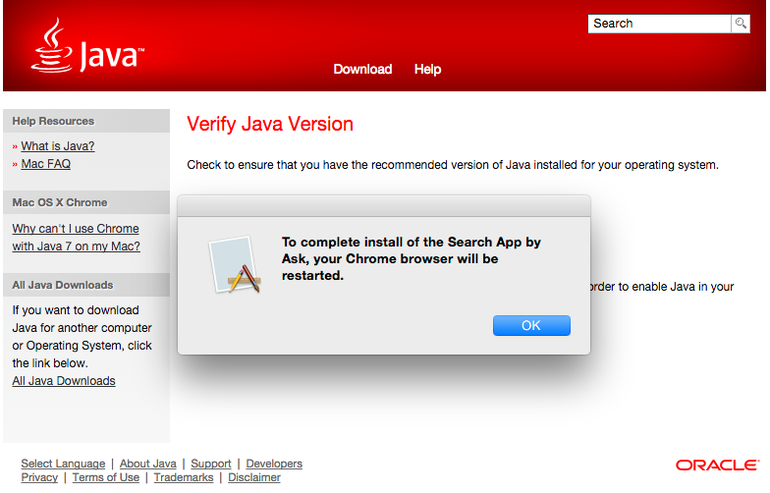
Image via ZDNet
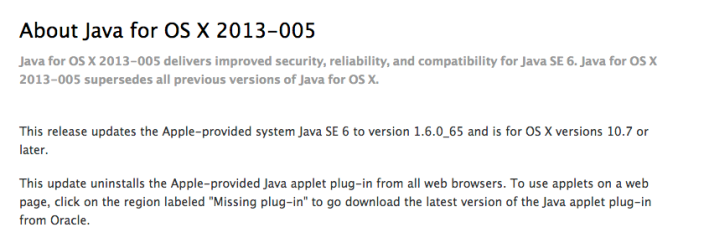
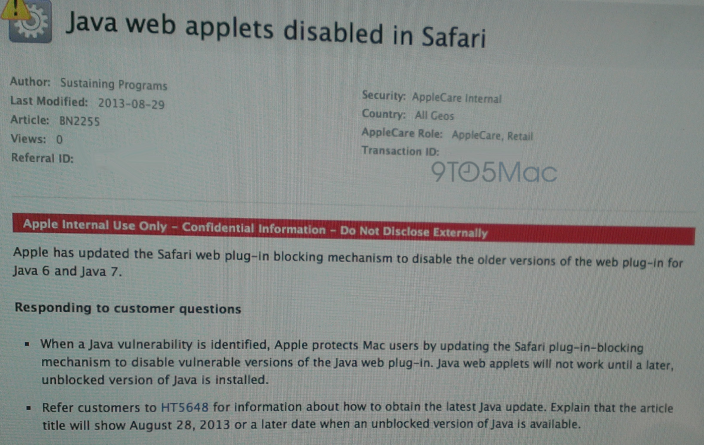
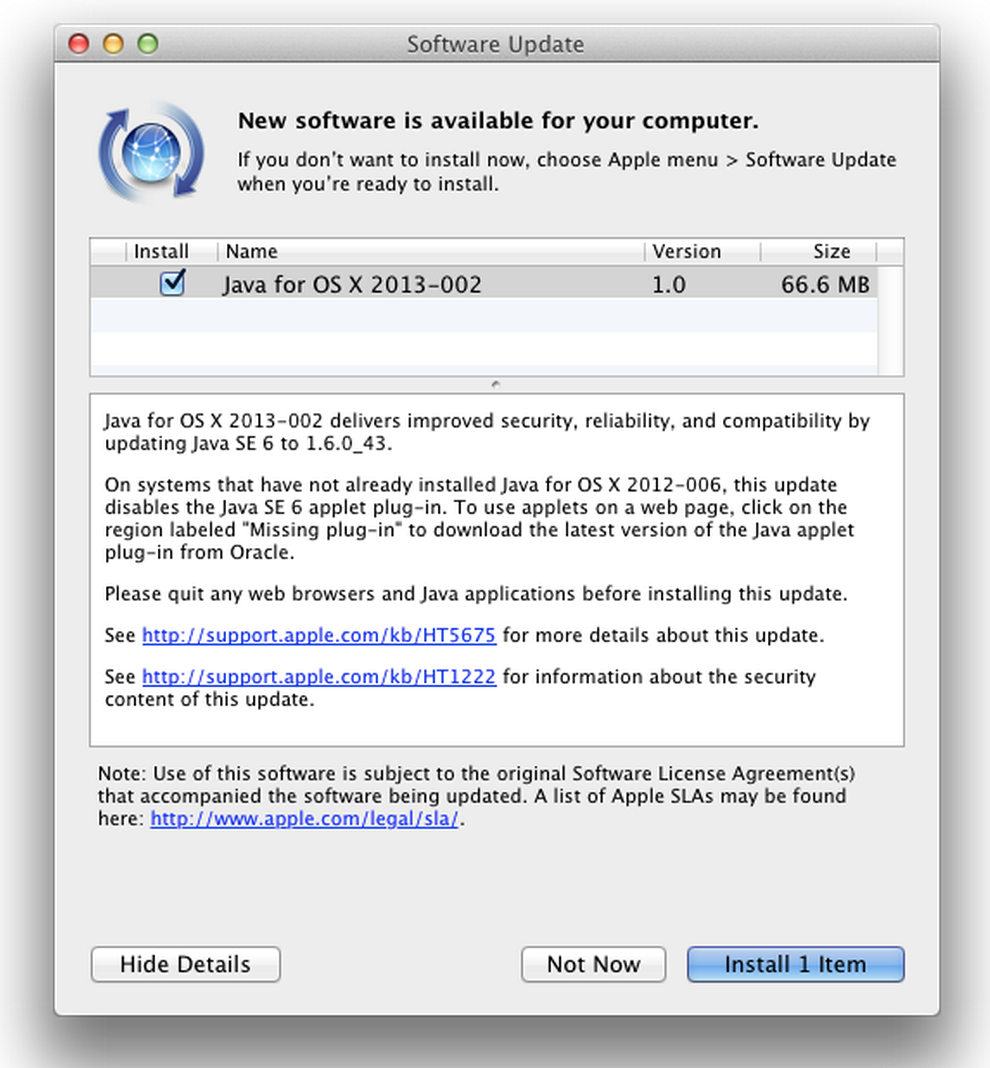
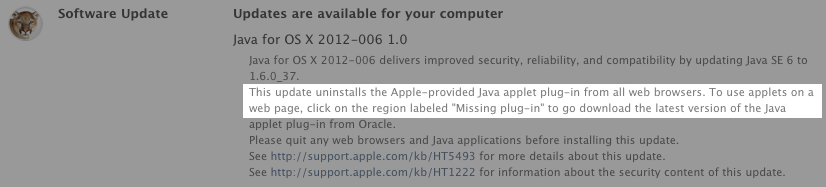
Windows users are likely already familiar with the adware that’s usually bundled with Oracle’s Java software, but for Mac users that annoyance has been mostly avoided. Unfortunately, ZDNet reports that today Oracle has updated its Java installer to include the Ask toolbar on OS X.
The installation process automatically changes users’ browser homepage to the nearly useless Ask.com, which is populated by ads and mostly irrelevant results. The software also installs an Ask browser toolbar. Since these changes are made by default during Java installation, those who don’t want these “useful” changes made to their computers will need to manually deselect the option during Java installation.
The changes seem to affect both Safari and Google’s Chrome browser. It may also impact some other third-party browsers. Even if you do install the adware, it should be fairly simple to remove the toolbar through your browser’s extension manager and change your home page back.