Apple’s head of security speaks out against iPhone app sideloading in new interview

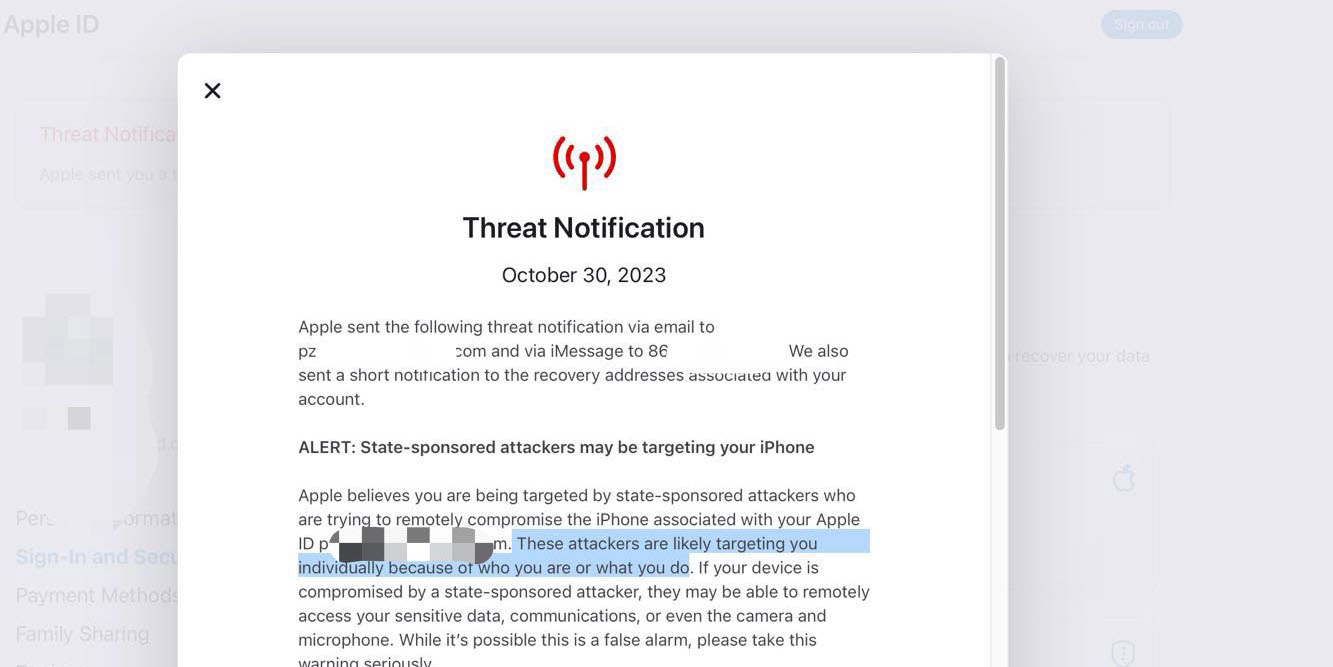
A new report from The Independent this weekend offers an interesting look at why and how Apple is “working hard to break into its own iPhones.” Ivan Krstić, Apple’s head of security engineering and architecture, spoke to The Independent for the report and explained why Apple feels the need to invest so heavily in security.
Notably, Krstić also addressed the possibility of Apple opening up the iPhone to third-party app stores and sideloading due to impending regulation in the European Union.
Expand Expanding Close